startx
Well if your have been into hacking since around 2012 you know the above headline is a linux command. I got taste of hacking/cybersecurity when I was very young teen. Teen from a middle class family who can’t afford to have internet connection over WiFi. Since in early days in India before Jio was a thing internet connection prices were high and one can only go to cyber cafe for 2-3 hours to surf internet. Nearby I have public park which is surrouded by many rich folks houses and apartments with good WiFi. At that time I had just got a Android tablet as a gift from my uncle returning from USA and badly wanted to download some apps over WiFi. So I had only one option is to get password access point near that public park. As usual curious kid I got to know about Backtrack 5 R2 (It is KaliLinux of older times from same Offesnive Security folks).
From Backtrack 5 I got my first taste of Linux environment and power of penetration testing. Basically startx was the command in BT5 to start your X-Org GUI and get into your desktop after login. These events took place around when I was 10th-11th grade high school kid. Yups I was indeed ScriptKiddie for sure just punching some random commands and hoping them to work all the time because I saw them working on YouTube or from NullByte’s blog.
systemctl start OSCP
Year passed I got into B.Tech Information Technology at university. From 1st year itself I was love with python programming used to make small automation scripts to run them on RaspberryPi 2. And during 2nd year I completed RHCSA (RedHat Certified System Administrator) by end of the 3rd year my programming, understading with linux OS and hacking with web techonologies were clear. By 2017 I was already teaching basics of penetration testing to many students and friends in my university. All the requirements seems aligned with me so I decided to purchase course and lab time for OSCP. I purchased 60 days of lab time. HTB was fairly new platform and Ippsec had just started making YouTube videos about retired machines. After complteing around 40 machines in lab and few boxes on vulnhub decided to sit for exam.
Timeline
- 2012 - 2015: ScriptKiddie type of self learning aka hacking for educational purposes XD
- 2015 - 2017: Serious learning about how computer works and learning hacking by active participation in infosec communities.
- Sep 2017: OSCP Course Purchase with 60 Days Lab Time
- March 2018: 1st Attempt (Beta Proctor Exam)
- Oct 2018: 2nd Attempt
- March 2019: Landed IoT Security Internship at SecureLayer7 and later join as full time
- 7th May 2020: 3rd Attempt which earned me the certification
My very first mistake was not to practice for buffer overflow seriously. I ended up failing exam with 2 fully rooted and one with user in my first attempt. The most tragic thing hanppened to me was passing of maternal grandmother. No one in my family informed me about it so I could focus on exam, and missed her funeral. She was one of the important person to me after my mother because whenever my single mother used to go out to earn money, she used to take care of me at home. I felt embarrassed and guilt for not passing exam after hearing heart shaking news about her.
In my second attempt I put lots of extra pressure on my self and made things complicated. Due to my axienty I did not solved any machine and give up shamelessly. I did try some hackthebox machines around 7 of active ones at that time. But my state of mind was not in right position. Next year everything seems to improve for me in my life, I got job in IoT Security at SecureLayer7. I was lucky enough to take that internship opportunity and show my potential all thanks to Nullcon (Biggest international cybersecurity confrence in India) where I meet them. So by working in idustry I had got pretty much idea about reaport making stuff professionally and methodolgies for penetration testing.
systemctl start exam
Well we all are aware of current global situation and COVID-19 pandemic. Due to abundance of free time, I decided to do something productive and only thing came into my mind of finish the chapter of OSCP. So yeah I decided to again fight this war with enough preparation and mindset. Here are the list of things I’ve done before exam. My exam date and time was Thu, 7-May-2020 5:30 PM
- Learned about windows stuff and some of it’s internals
- Powershell scripting and working with WMI Objects
- HTB machines active ones for 2 weeks, I set goal of achieving good rank and I ended up having Pro Hacker rank
So after doing above things holes in my knowledge were filled, was feeling confident. I had focused mindset of not giving up and keep reminded my self life long message of not giving up from my grandma. She was once board exam topper and used to study under street lamp, not to mention her passion in biology subject where she had slept near skeleton in college lab (also became well qualified government recruited nurse). All her life examples give me strength and make me forgot my excuses that, today we have tons of resources to practically pass any cybersecurity certs by learning stuff online and having comfort of home.
I charted my exam plan on whiteboard and kept it in front of me.
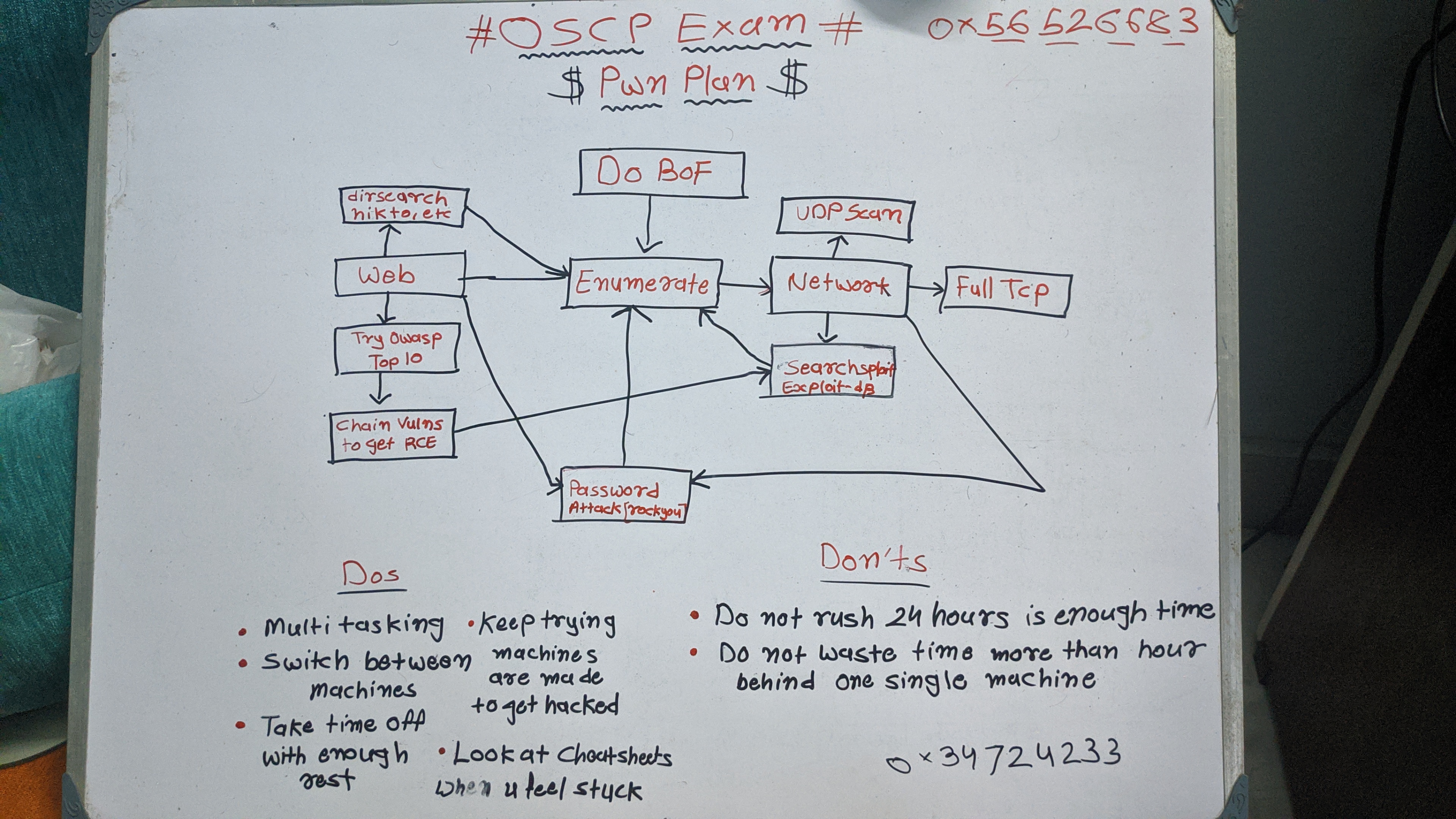
War plan
The best tips about time management by far I found were from this video on YouTube watch till end.
For buffer overflow this video is easy to grasp, made by one of my online friend. We meet in IRC student chat during my first attempt.
My notes for buffer overflow can be found here. For note taking I use Joplin, it’s really nice open source software for maintaining information about tasks in markdown. And best thing about it is that you can sync everything accross all deviecs and cloud drives. Also used it during exam as well, helped to see data on my phone while I am off the screen for short breaks.
Yes learn markdown, it’s not really hard. Once you master it you will love it and evetually write everything in it. And indeed my entire blog is written in markdown to be honest. I wrote my final exam report using this markdown template https://github.com/noraj/OSCP-Exam-Report-Template-Markdown. It uses pandoc backend in which at start of mardown file you can configure various settings, these are written in yaml syntax. My settings were given below.
---
title: "Penetration Test Report for PWK Certification Exam"
author: ["[email protected]", "OSID: OS-32029"]
date: "2020-05-07"
subject: "Markdown"
keywords: [Markdown, Example]
subtitle: "OSCP Exam Report"
lang: "en"
titlepage: true
titlepage-color: "A90C1C;"
titlepage-text-color: "FFFFFF"
titlepage-rule-color: "FFFFFF"
titlepage-rule-height: 2
logo: offsec-logo.png
book: true
classoption: oneside
code-block-font-size: \scriptsize
---
And some of my tweaks with pandoc command to enable synatx highlight on my bash commands. Syntax definition file here. The best place to learn about all these settings are pandoc manual itself ttps://pandoc.org/MANUAL.html
pandoc OSCP-exam-report-template_whoisflynn_v3.2.md \
-o OSCP-OS-32029-Exam-Report.pdf \
--from markdown+yaml_metadata_block+raw_html \
--template eisvogel \
--table-of-contents \
--toc-depth 6 \
--number-sections \
--top-level-division=chapter \
--highlight-style tango --syntax-definition bash.xml
Pwn approach
- First I did BoF in 2 hours, I made python and go programming script as final exploit.
- Then I got user on 25 marks machine in 1 hour, and in next hour got root. Root was really fun I thought some creative way and dang pushed my ssh keys with exploit and got fully working root shell over ssh. I did it with other machines as well, always prefered to push ssh keys whenever came accross linux box so I can have fully interactive shell.
- I was bit exhausted after dinner I turned to easy box and that too I completed in around 50 min. So I had 60 marks in 5 hours in exam.
- For all night I stuck with rabit hole on machine and was stuck with user, so had some sleep between 4AM to 9AM.
- By 11 no progress so I decided to switch to other 15 marks machine and that paid of. At 3PM I got root. Final score was going was 90 and worst case was 85, so yeah I knew my goal was achieved and had great sleep in evening. And entire night I kept wiriting report cross checking everything including my screenshots and flag hashes. Ended up with 52 pages final exam report.
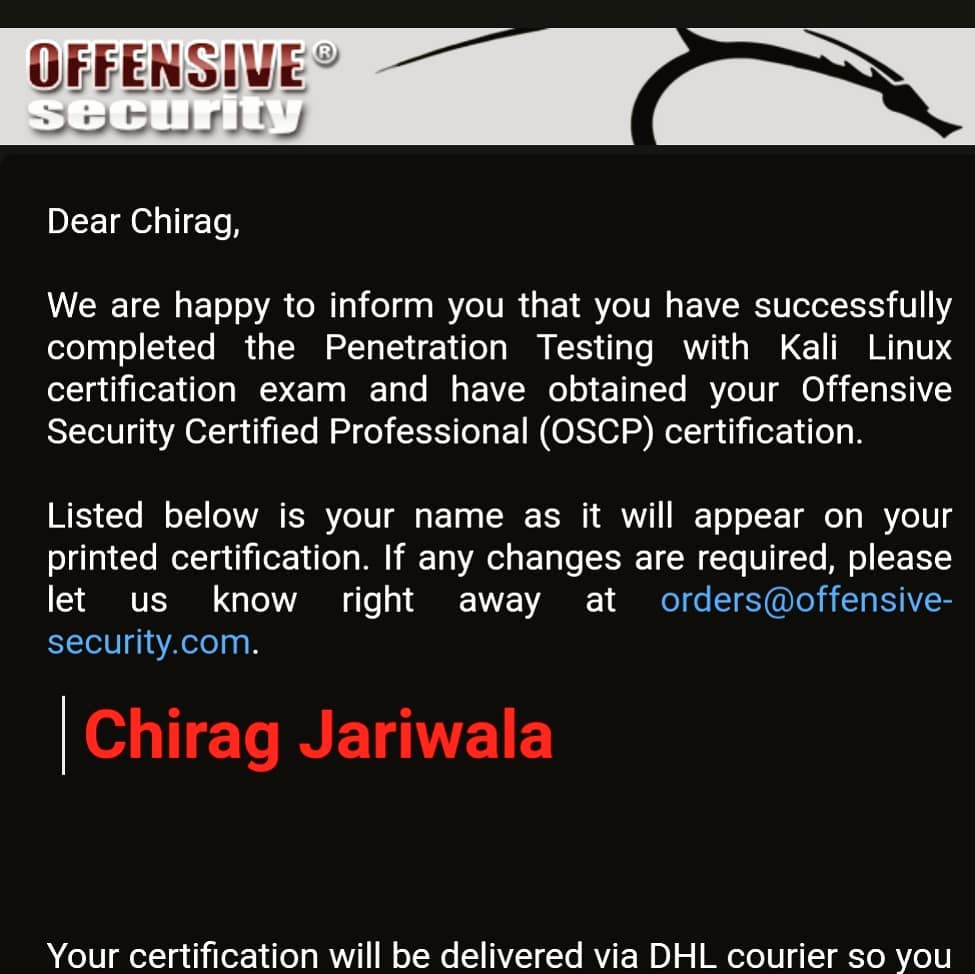
After few days got my result at 14th-May 6:19PM and satisfaction to my soul. All years of hardwork and sacrifices paid off learned tons of things along the path. OSCP is not just a certification it’s journey to discipline and excellence in cybersecurity career. My heart goes out to all OSCP exam takers who are reading this blog, don’t give up if you fail. Try again and most importantly Try Harder! and you will get this too https://www.youracclaim.com/users/chirag-jariwala
sudo shutdown now
That’s all I want to say. There are far better out there which points to great learning reaources for OSCP exam, so I wanted to just tell my story and experince to provide some fuel to your motivation. You can reach me out on twitter or linkedin anytime if you want to ask something and have doubts regarding exam preparation.