Update For this blog
After nearly a long ago of sharing insights on IoT security, I’ve made the difficult decision to sunset my personal blog. This choice stems from evolving personal responsibilities, shifting professional demands, and significant changes in Canada’s immigration landscape that have reshaped my daily life. The Weight of Competing Priorities Immigration Policy Shifts: Canada’s 2025 immigration reforms introduced stricter caps on permanent residents (reduced to 395,000 from 485,000) and heightened requirements for temporary workers....
Journey from nothing to OSCP
startx Well if your have been into hacking since around 2012 you know the above headline is a linux command. I got taste of hacking/cybersecurity when I was very young teen. Teen from a middle class family who can’t afford to have internet connection over WiFi. Since in early days in India before Jio was a thing internet connection prices were high and one can only go to cyber cafe for 2-3 hours to surf internet....

My review on Centrifuge a firmware analysis platform by ReFirm Labs
Story It was yet another boring day in COVID-19 lockdown and I was checking my Linkedin. Did not knew small surprise connection request is waiting. It was from one of the Co-founders of ReFirm Labs Mr. Terry Dunlap. Without hesitation I accepted request and started talking, he has very humble personality with years of experience in cybersecurity. In between conversation I mentioned binwalk and that I use it for day to day manual firmware analysis....
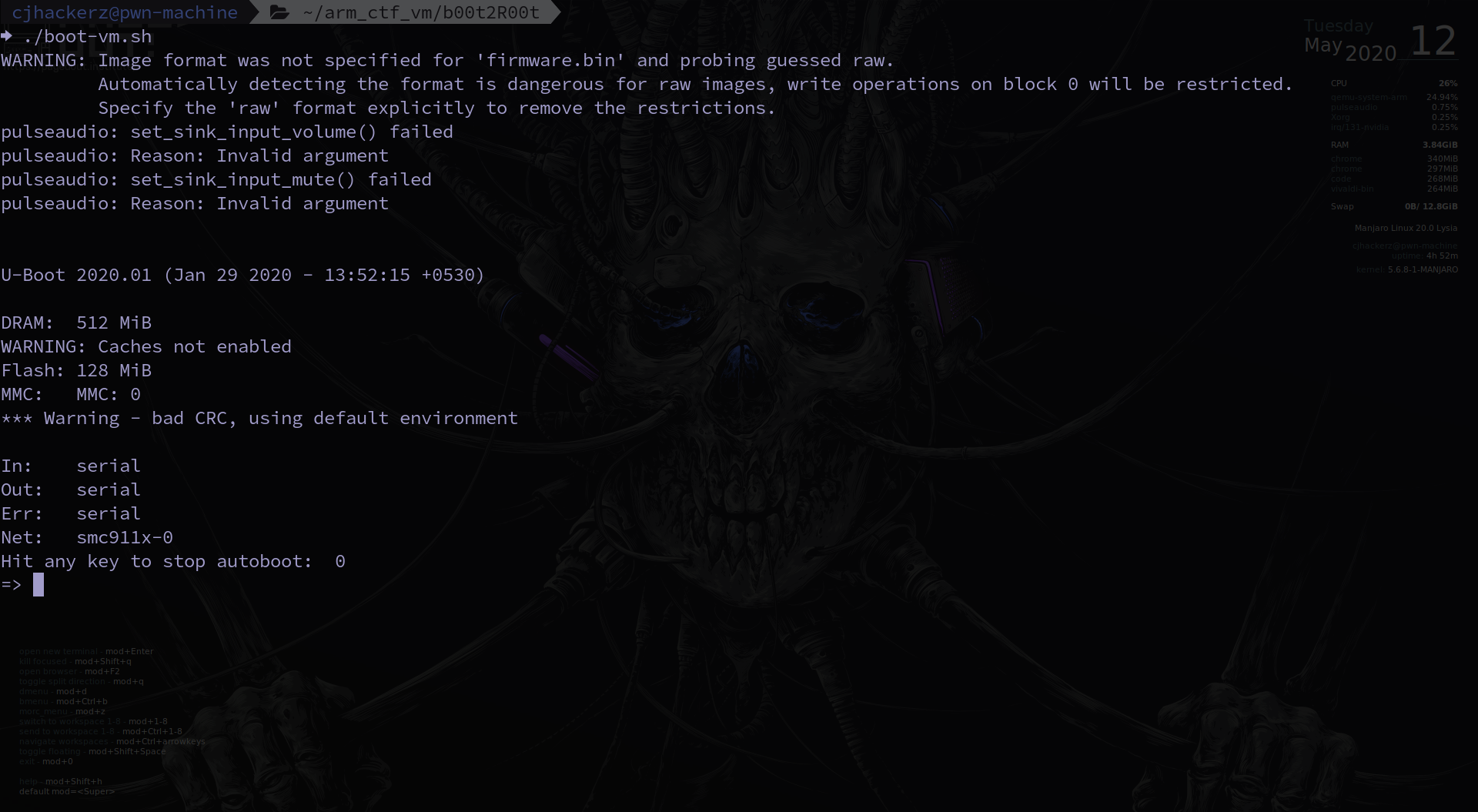
Understanding how bootloader works by creating your own firmware
Getting started with memory layouts So in previous blog post on solving CTF challenge created by me on real alike firmware, I did not touched subject of u-boot bootloader in depth and how such firmware was created in first place. Welcome back here again today you will see steps to create your own firmware for qemu and making it work with u-boot. Many of the stuff you might have encoutered during computer science class and you will be amazed how the concepts of fundamental system architecture and operating system works in action....
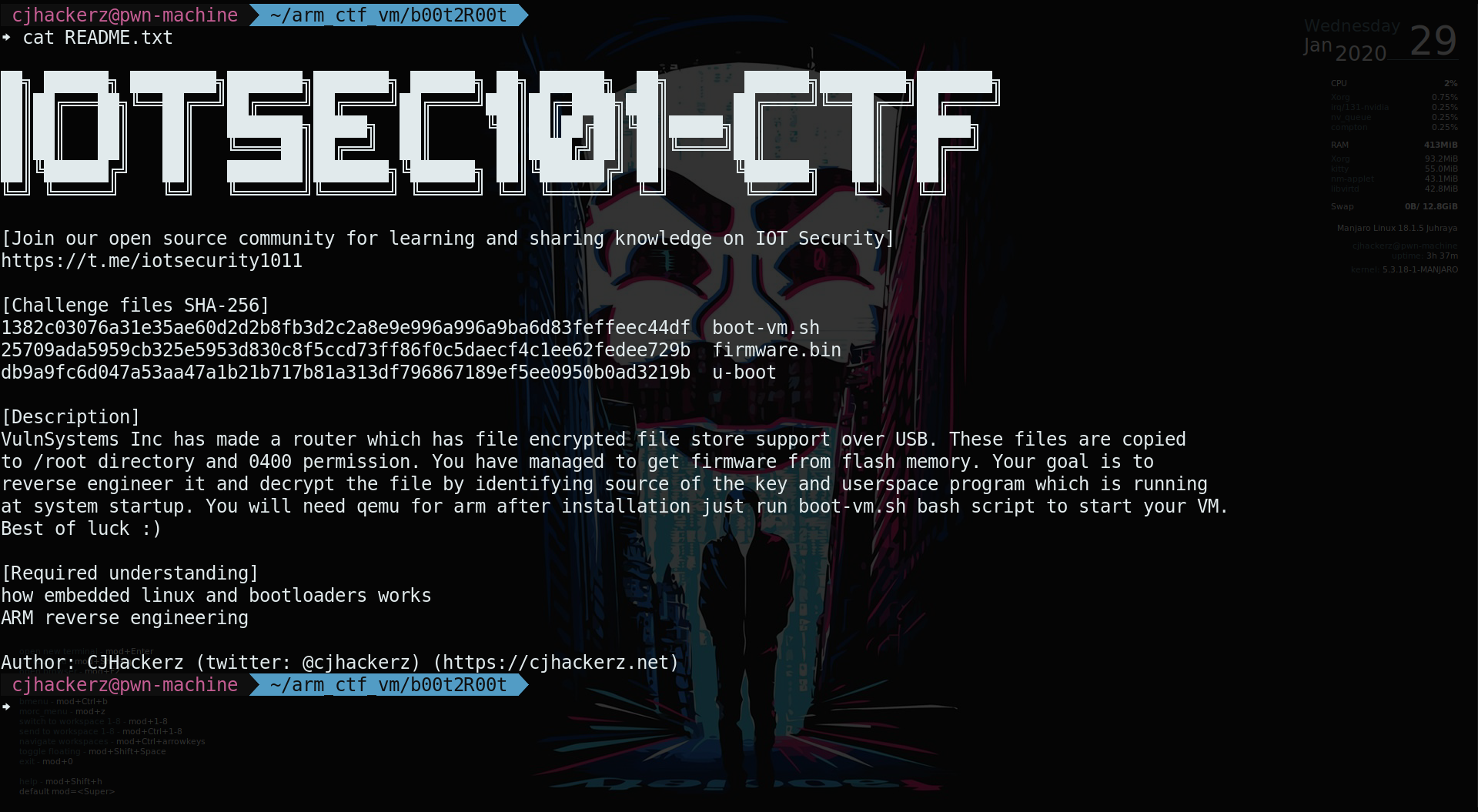
WriteUp: First ever real like simulated IoT security challenge
Few months ago I had released a challenge on IoT/Embeded security and put it up on various places inorder to allow people to solve it. Sadly long wait is over and now covid-19 in on rise gloablly there is no interests to solve it even in quarantine. So to give justice to my work I am putting up this write up together which you can follow along to learn and solve my challenge....
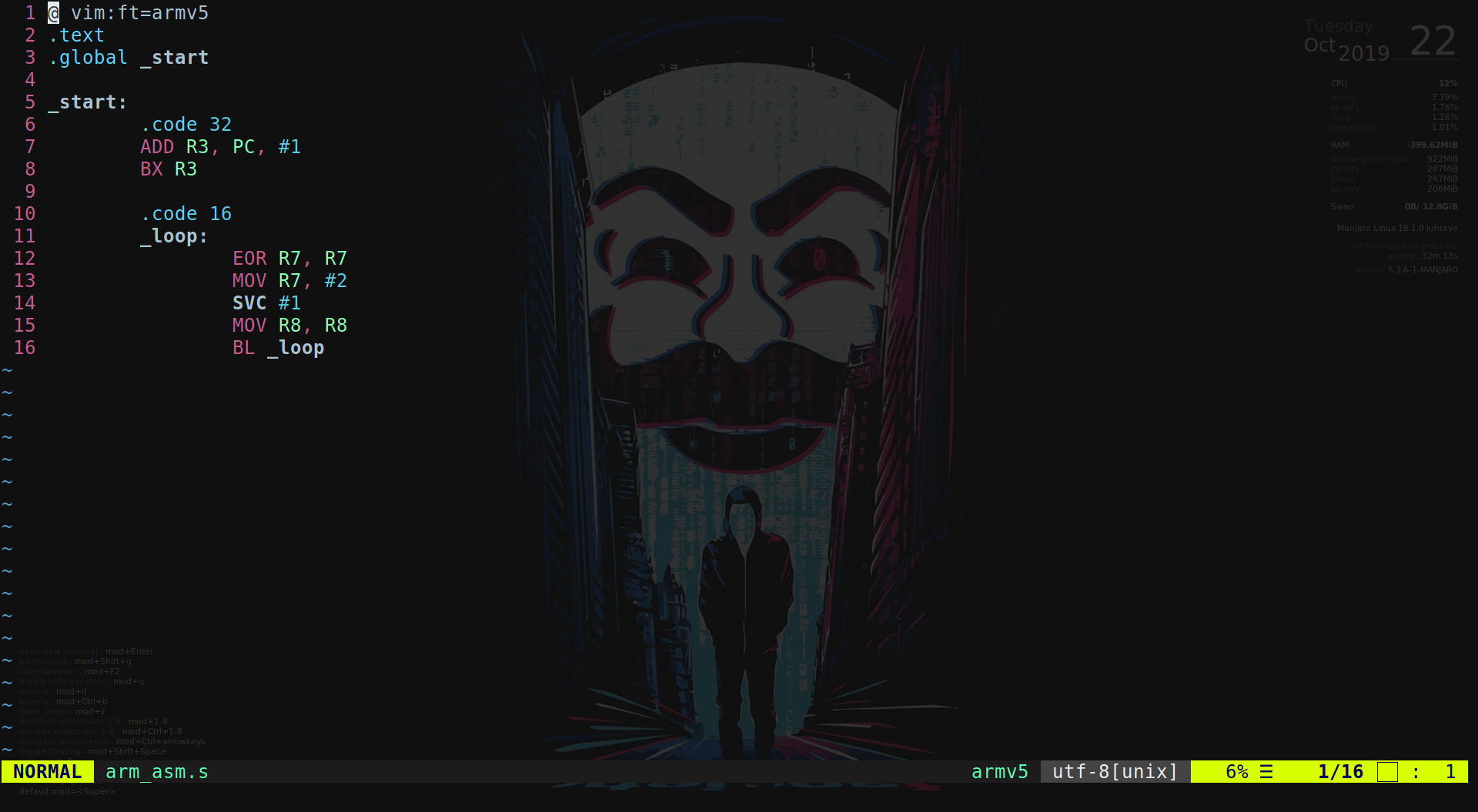
An overview on writing ARM shellcode
\0x53\0x54\0x41\0x52\0x54 Last month was really productive month that I had in my life after college graduation, I end up learning so many new things also did hands on session on CAN-bus forensics with one of the oldest hacker community called Garage4Hackers. Alongside that I learned a lot about ARM architecture from Azeria with her blog. Also lot’s stuff related to learning ARM assembly is available online that’s why I am not gonna write entire blog series ARM assembly instead in this article I will just walkthrough ARM shellcoding subject from an introduction point of view....
ARM and MIPS emulated lab setup for IoT security in Qemu
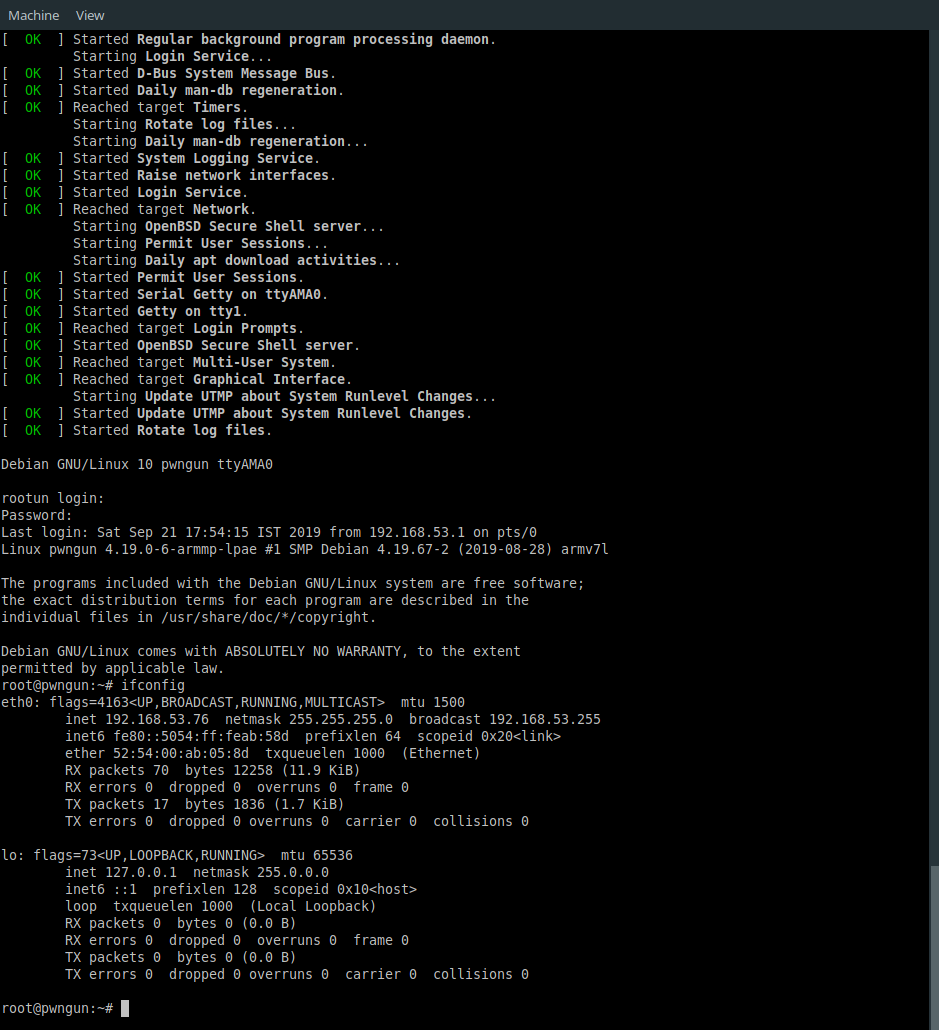
Backstory After poking around entire internet for a month, I finally managed to learn how Qemu works in general. There already lots of tutorial out there on how to setup ARM and MIPS based machines inside Qemu but I personally feel those are incomplete guides and does not touch the subject deeply. So that’s exact reason for wirting this article giving clear explanation about everything you will need to know inorder to have ARM and MIPS based Qemu virtual machine with full NAT networking support....
CAN-bus protocol pentesting and forensics
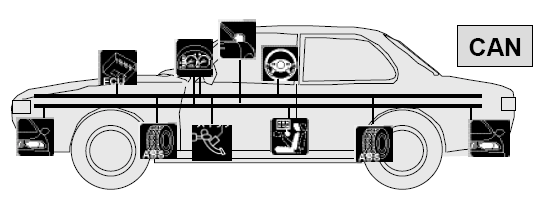
Introduction CAN (Controller Area Network) is a vehicle bus protocol standard which allows microcontrollers and ECU (electronic control units) to communicate which each other without a host computer. It is a message-based protocol, designed originally for multiplex electrical wiring within automobiles to save on copper, but can also be used in many other contexts. But why CAN you may ask, because it’s low-cost error less since via single CAN interface ECU can communicate with each through the centralized system with less wiring involved and data is transferred over digital signal instead of analog so it reduces chances of error occurrence....
Reading data from EEPROM without desoldering
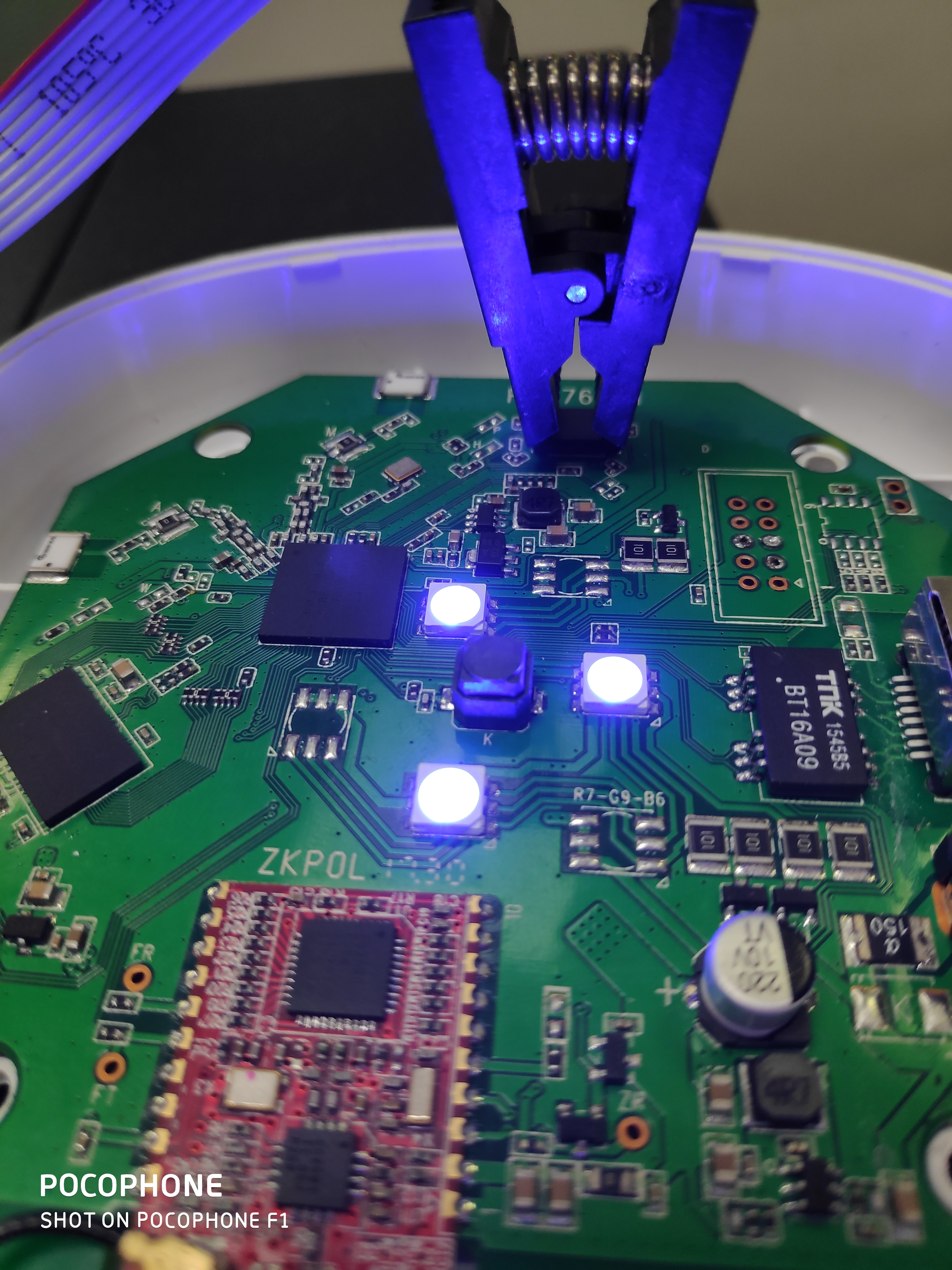
Introduction In IoT/Hardware security it is common practice of dumping firmware/bootloader data inorder to perform reverse engineering for closed source system applications. Well known easiest way is to download .bin/.zip (packed firmware) files from device manufacturer’s website which they provide to end users for firmware upgrade operations. And later us hackers/security researchers throw these files to reverse engineering softwares such as binwalk to check it’s contents and extract the needed stuff....
UART using Bus Pirate
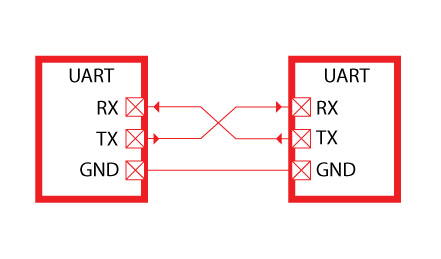
title: “Mqtt pwn” date: “2018-05-06” tags: [“GPS data leak”, “MQTT”, “IoT”, “Cybersecurity”] description: “GPS data leak from in owntracks due to CVE-2017-7650 and poor ACL config in MQTT brokers” ShowToc: true TocOpen: false Introduction UART stands for Universal Asynchronous Receiver/Transmitter. It’s not a communication protocol like SPI and I2C, but rather a physical circuit which transmits and receives serial data. UART transmit data asynchronously, which means there is no clock signal to synchronize the output of bits from the transmitting UART to the sampling of bits by the receiving UART....