Story
It was yet another boring day in COVID-19 lockdown and I was checking my Linkedin. Did not knew small surprise connection request is waiting. It was from one of the Co-founders of ReFirm Labs Mr. Terry Dunlap. Without hesitation I accepted request and started talking, he has very humble personality with years of experience in cybersecurity. In between conversation I mentioned binwalk and that I use it for day to day manual firmware analysis. Suddenly he pointed me out Centrifuge a firmware analysis platform which they have developed very recently.
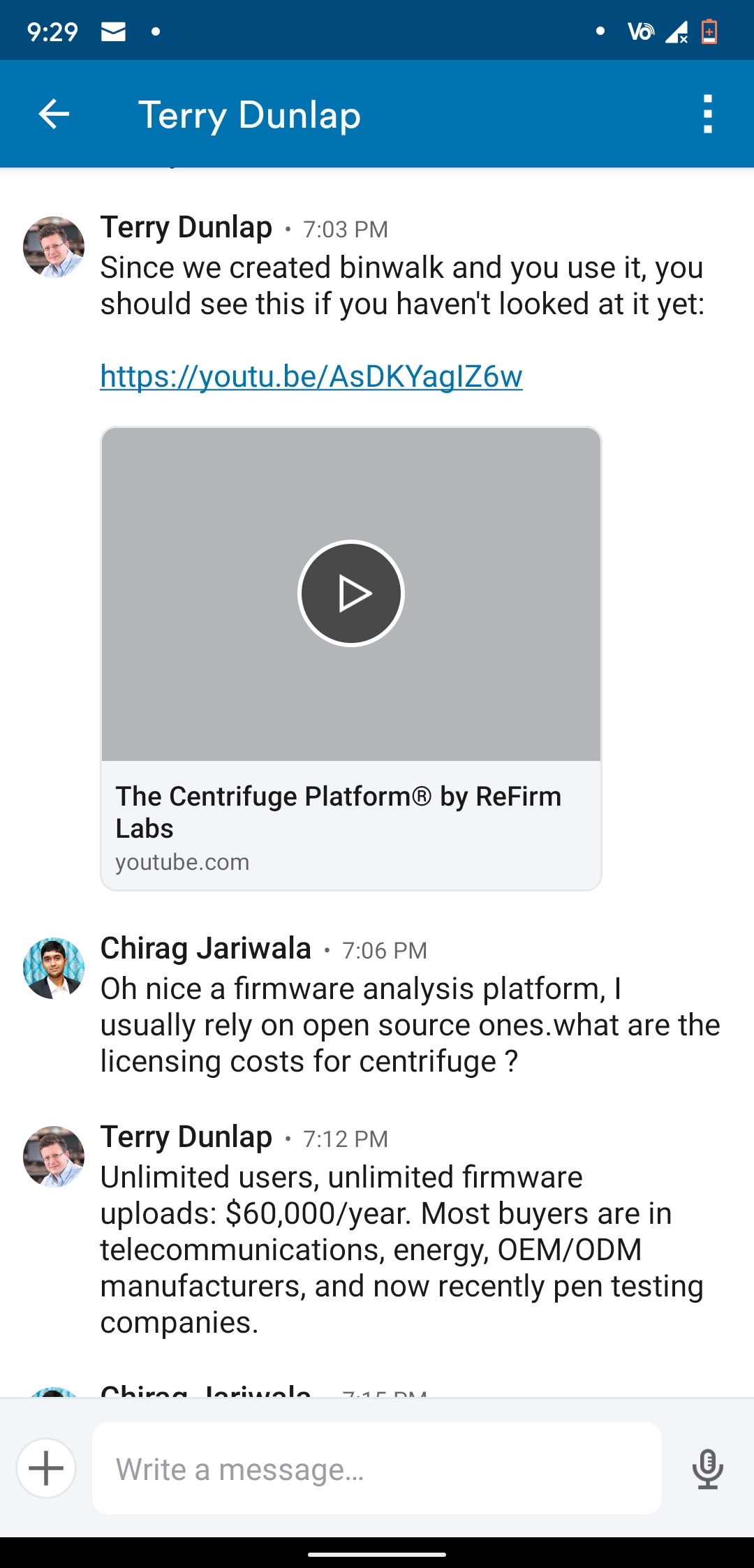
Conversation screenshot
Yes it costs for full access to this product. Sounded like a dream to me that I ever use this platform. And as he clearly mentioned it’s meant for companies who work with IoT product development and IoT security not for individual security researchers/bug bounty hunters in IoT security. After few texts he decided to give me trial account with 3 firmware upload limit and review it. So here I am, this is my honest review on firmware analysis platform called Centrifuge by creators of binwalk ReFirm Labs and it is really good.
Test scenario
For testing this platform I picked up 3 router firmwares. One from Netgear, one from Cisco Linksys and my very own custom created. All older netgear products tends to have some kind of vulnerability and it is vendor that I consider having most vulnerabilities in routers after D-Link routers. Linksys devices tends to be bit safe since they are seems to build with security in mind from very start. And custom firmware I have created latest softawre components right from the kernel (see my previous blog post).
| Vendor | Product | Type | Firmware version |
|---|---|---|---|
| Netgear | WNR2000v5 | N300 Wireless Router | 1.0.0.28 |
| Linksys | E900 | N300 Wireless Router | 1.0.09.002 |
User interface
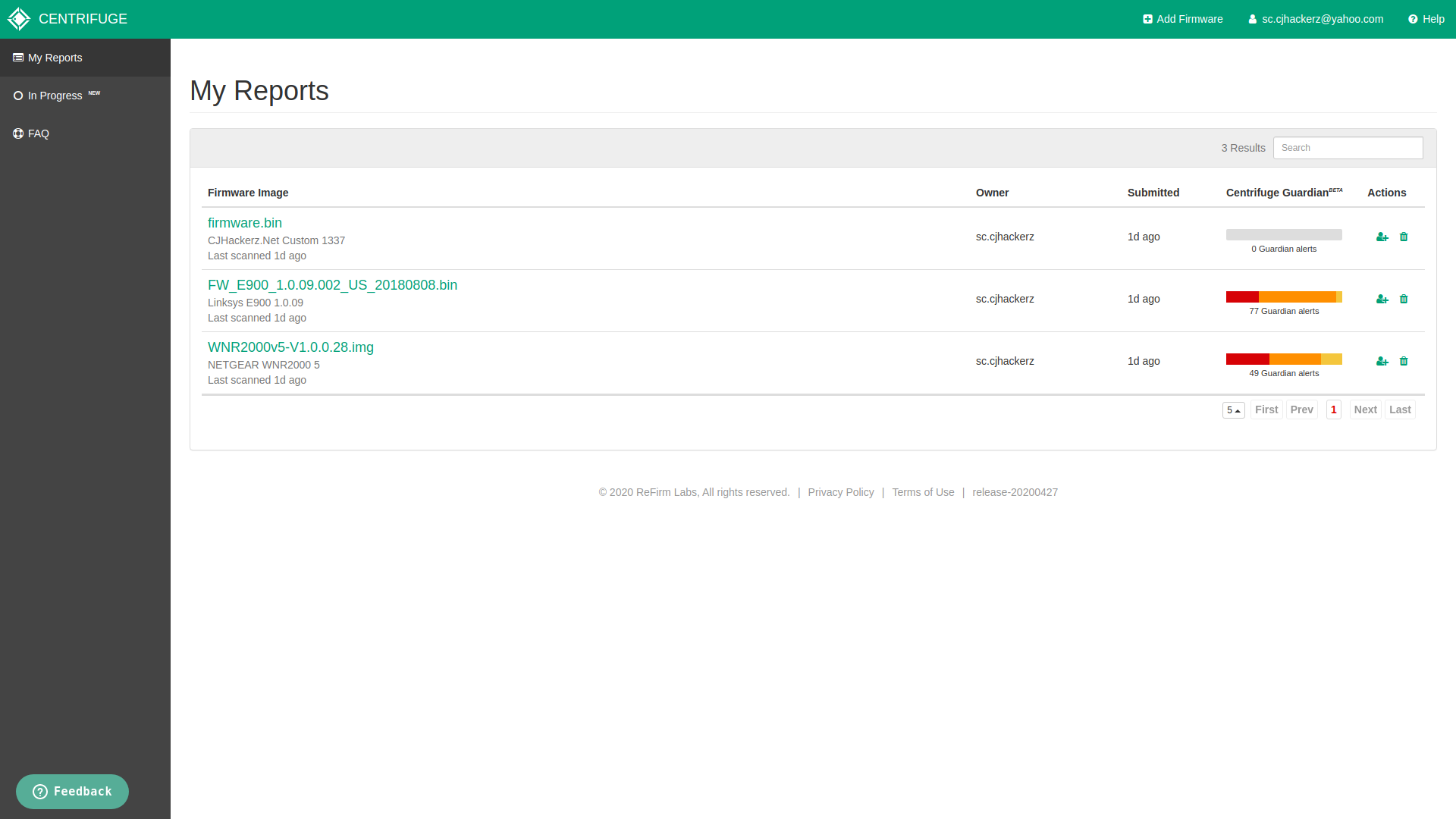
Key to success for any product is user interface. Centrifuge has on the point UI which is very easy to use. After login you can start uploading firmware by clicking Add Firmware button on top right corner or see the reports of previously uploaded firmware. I am not UX/UI expert but whenever I use any such platform all I want is interface that makes sense and I don’t have to seek support. Which is infact true for Centrifuge. But dark mode is missing which helps to work during night time.
UI Design
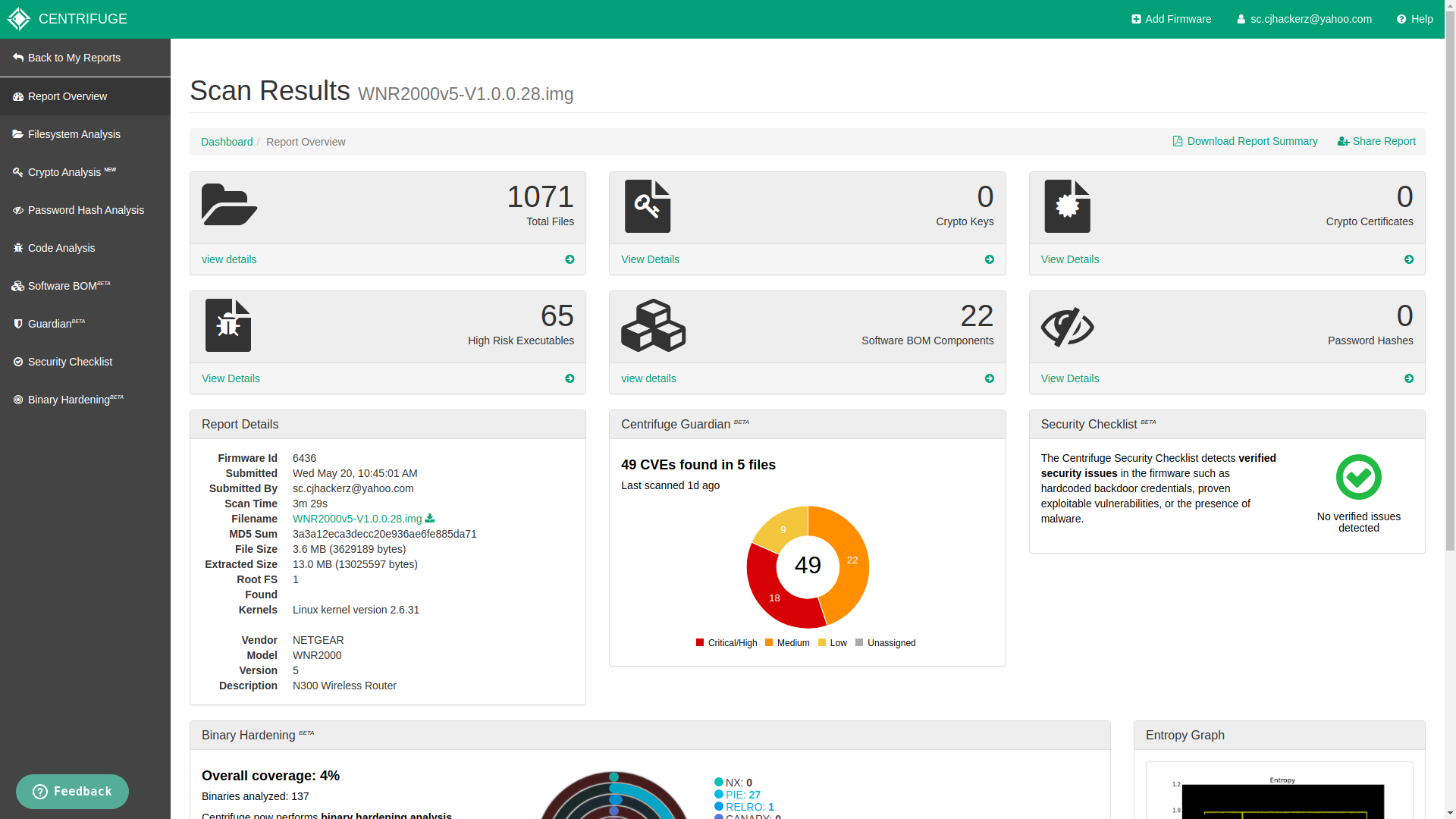
Report overview dashboard
Technical overview
Big advantage of using Centrifuge is that your hosting infrastructure is managed by ReFrim labs with tech support included. You don’t have to worry about configuration and deployment at all. Purchase the license, you get access and leave it to your employees. It has well written API documentation. Everything seems to be implemented in their API which makes integration easy with CI/CD pipeline in DevSecOps.
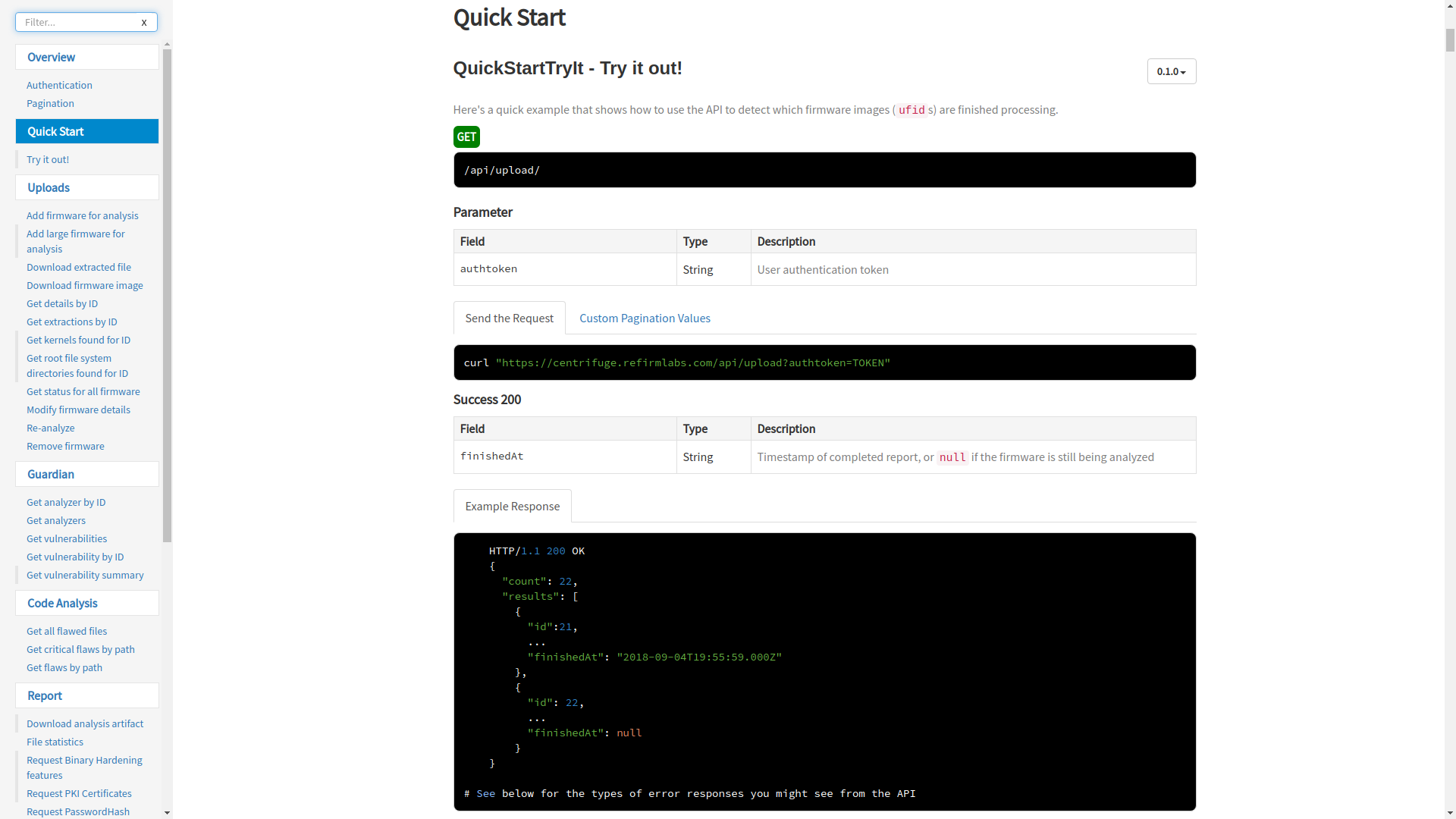
API Docs
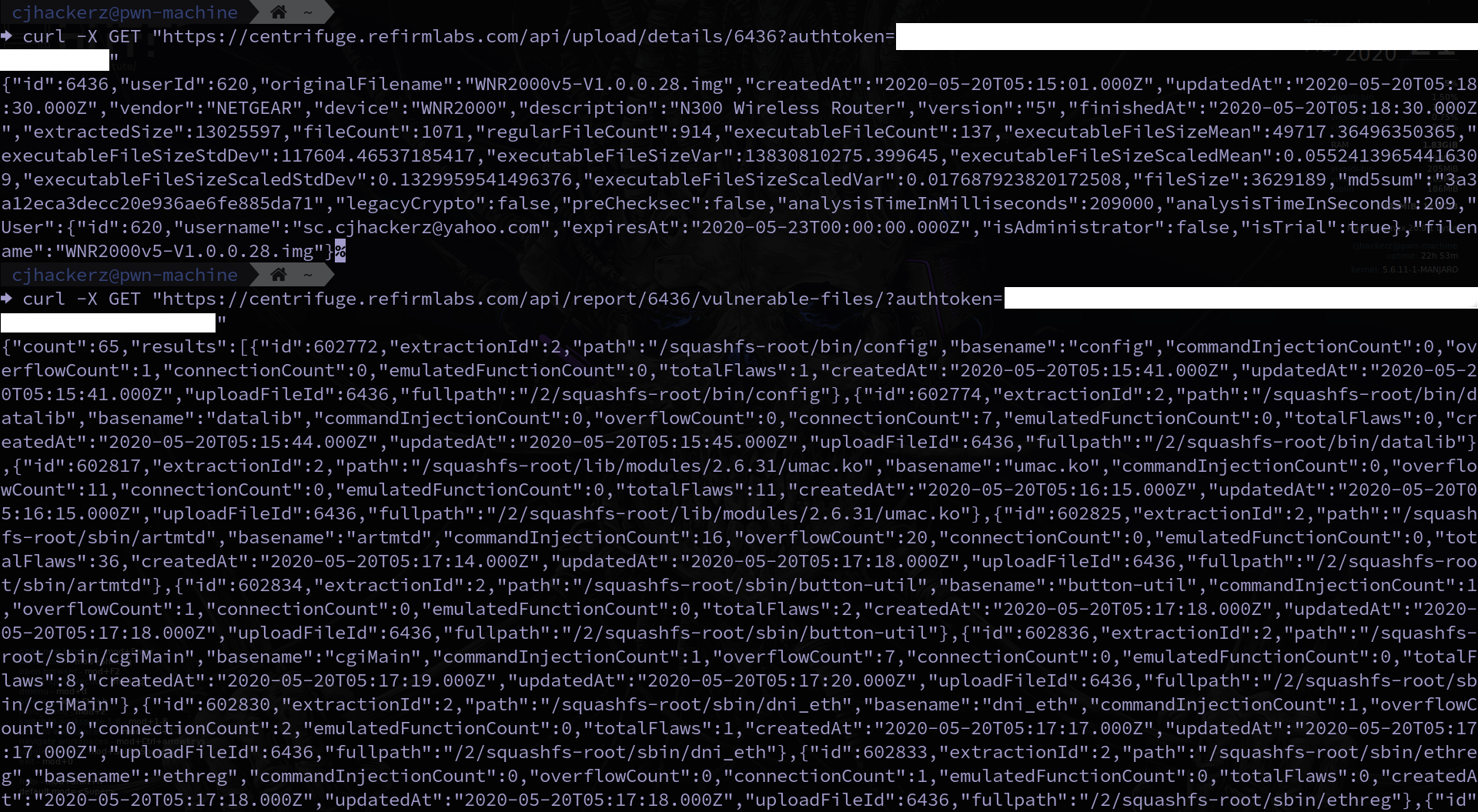
Output from API requests
Currently it has following list of features:
- Filesystem Analysis (file browser for extracted filesystem)
- Crypto analysis (finds private and public keys along with SSL certs)
- Password Hash Analysis (gets password hashes for active users on system)
- Code Analysis (gives you list of potentially vulnerable function calls for buffer overflow and command injection at particular offset address inside binary)
- Software Bill of Materials (identifies list of softwares components inside firmware)
- Centrifuge Guardian (looks for publicaly known vulnerabilities from CVE databases)
- Security Checklist (performs exploit scan, backdoor scan and malware scan)
- Binary Hardening (gives overview about binary level protections on executables and libraries)
Filesystem Analysis
This allows you to browse extracted contents from packed firmware file. You can see root filesystem folders and download it as well.
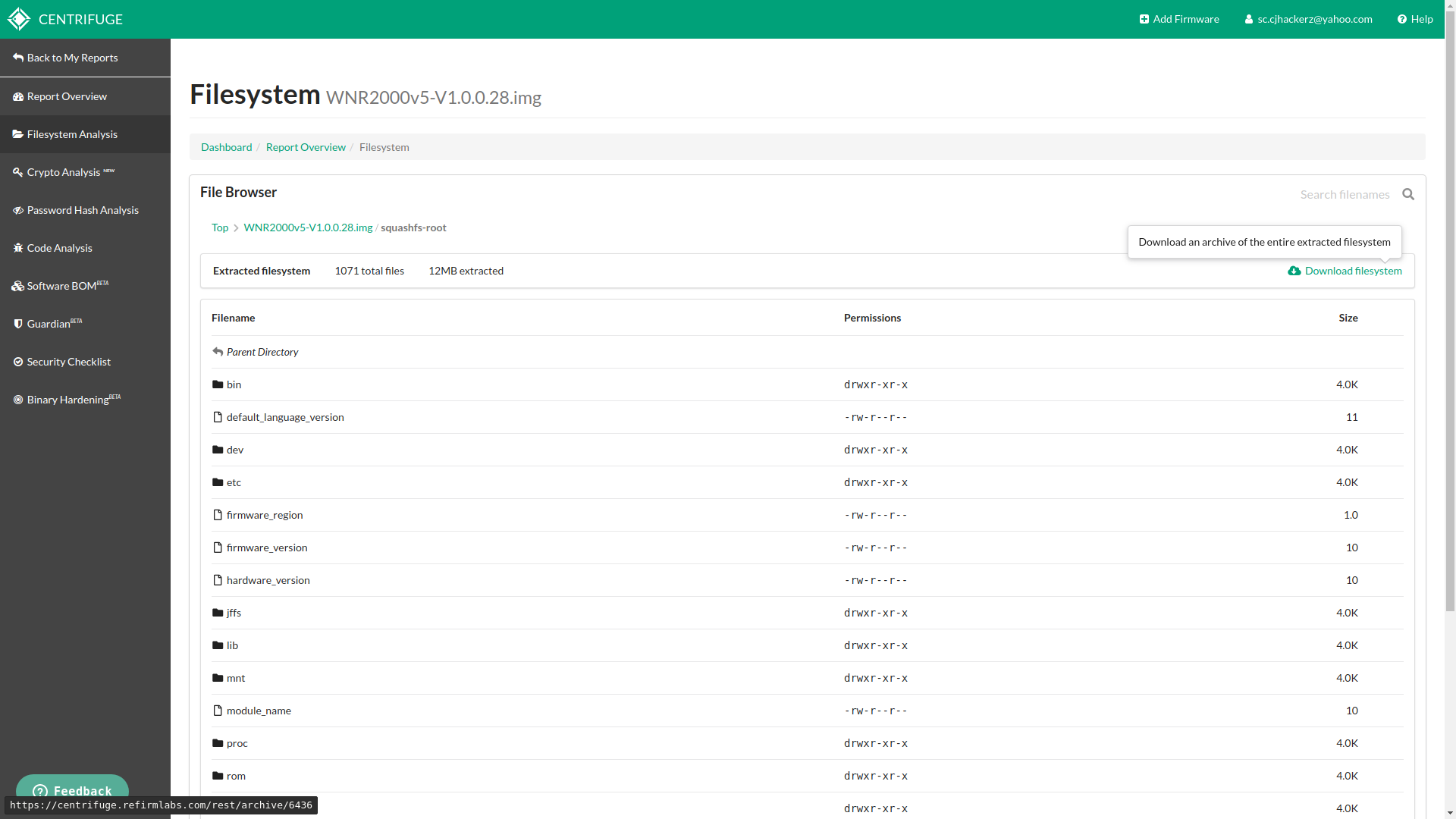
Output from API requests
Crypto analysis
If firmware has network or web service which has feature to encrypt your traffic over SSL/TLS, such environment relies on encryptions key pairs. From public/private key analysis one can indentify flaws in key generation system or usage of weak crypto algorithms. Basically this feature is useful for doing cryptanalysis on crypto oriented operations inside given firmware. With my Linksys firmware file it was able to successfully find private key responsible to encrypt traffic for HTTPS access to router’s admin panel. I know this because I own this device as well.
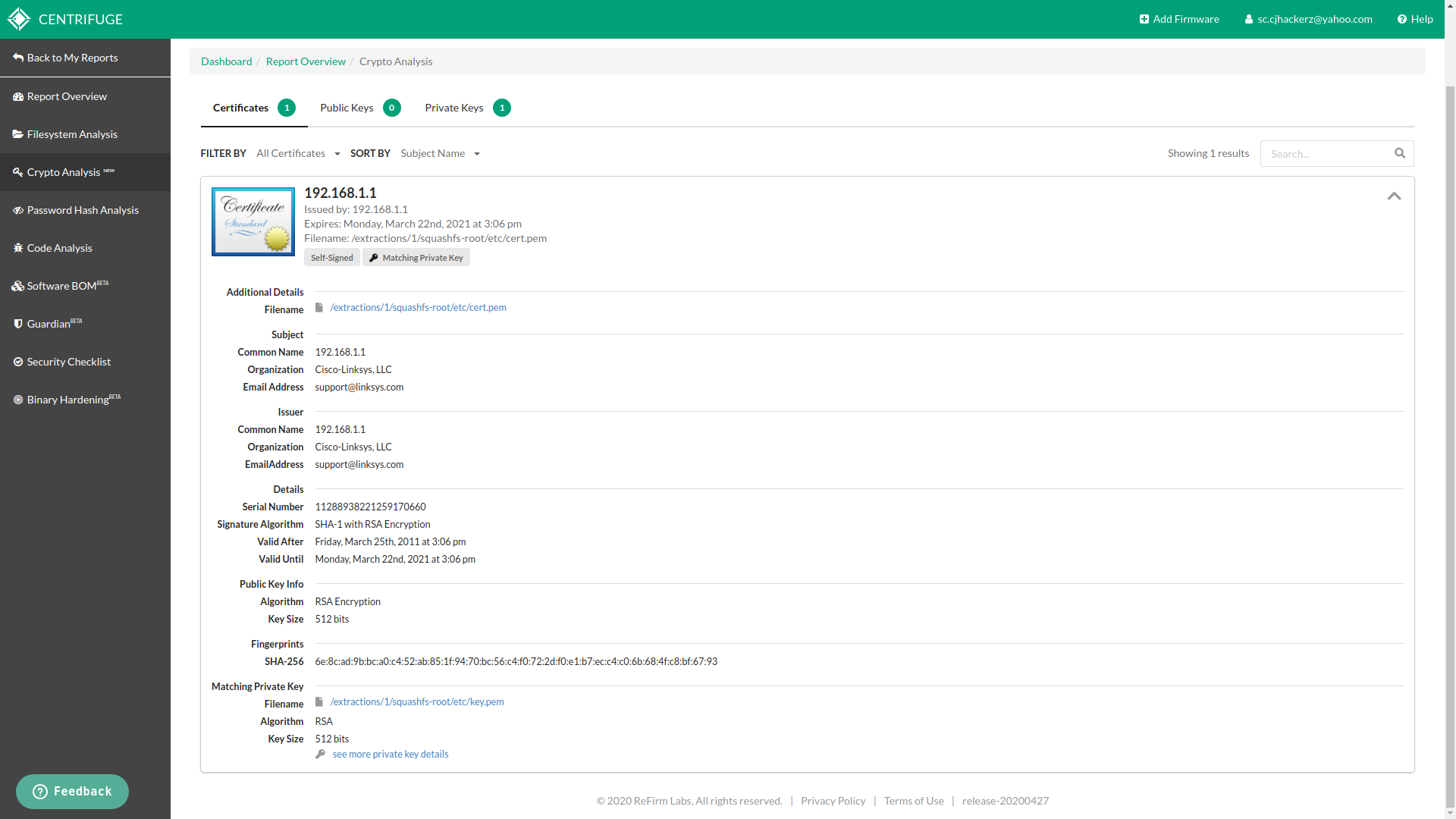
Web server cert
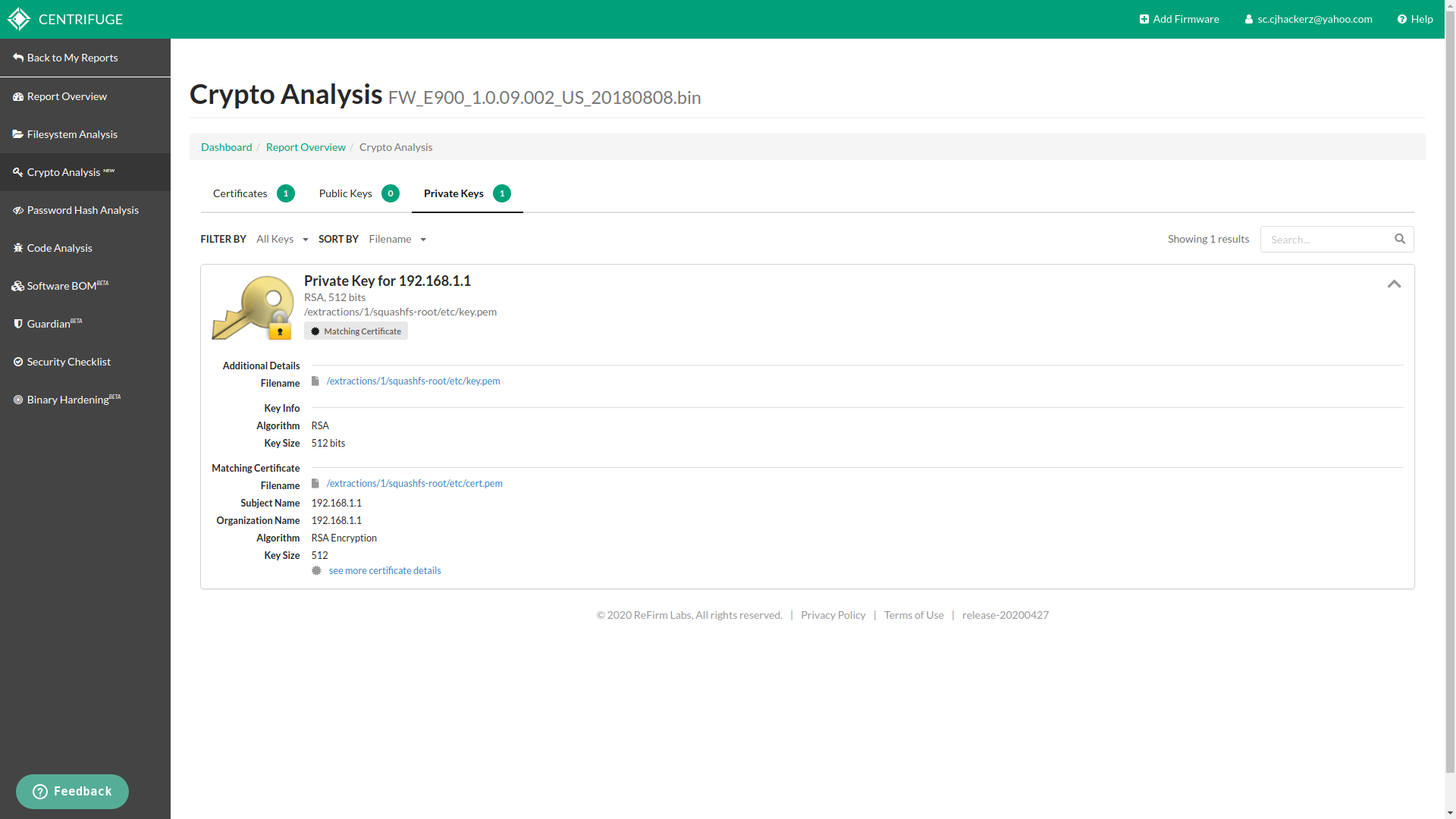
Private key for certificate
I was shocked to see my very own router uses 512 bits key length for HTTPS communication. Any one can bruteforce public key provided by router in same network and gets credentials of admin panel with help of MITM attacks.
Password Hash Analysis
My custom firmware had root password set as realtek which I picked from SecLists repository file Passwords/Default-Credentials/telnet-betterdefaultpasslist.txt. This feature does not crack passwords with tools like John the Ripper and Hashcat it will be shown as original hash and cracking reponsibility is left upto security analyst. I personally execpted it to crack password for me by looking at deafult passwords lists from SecList.
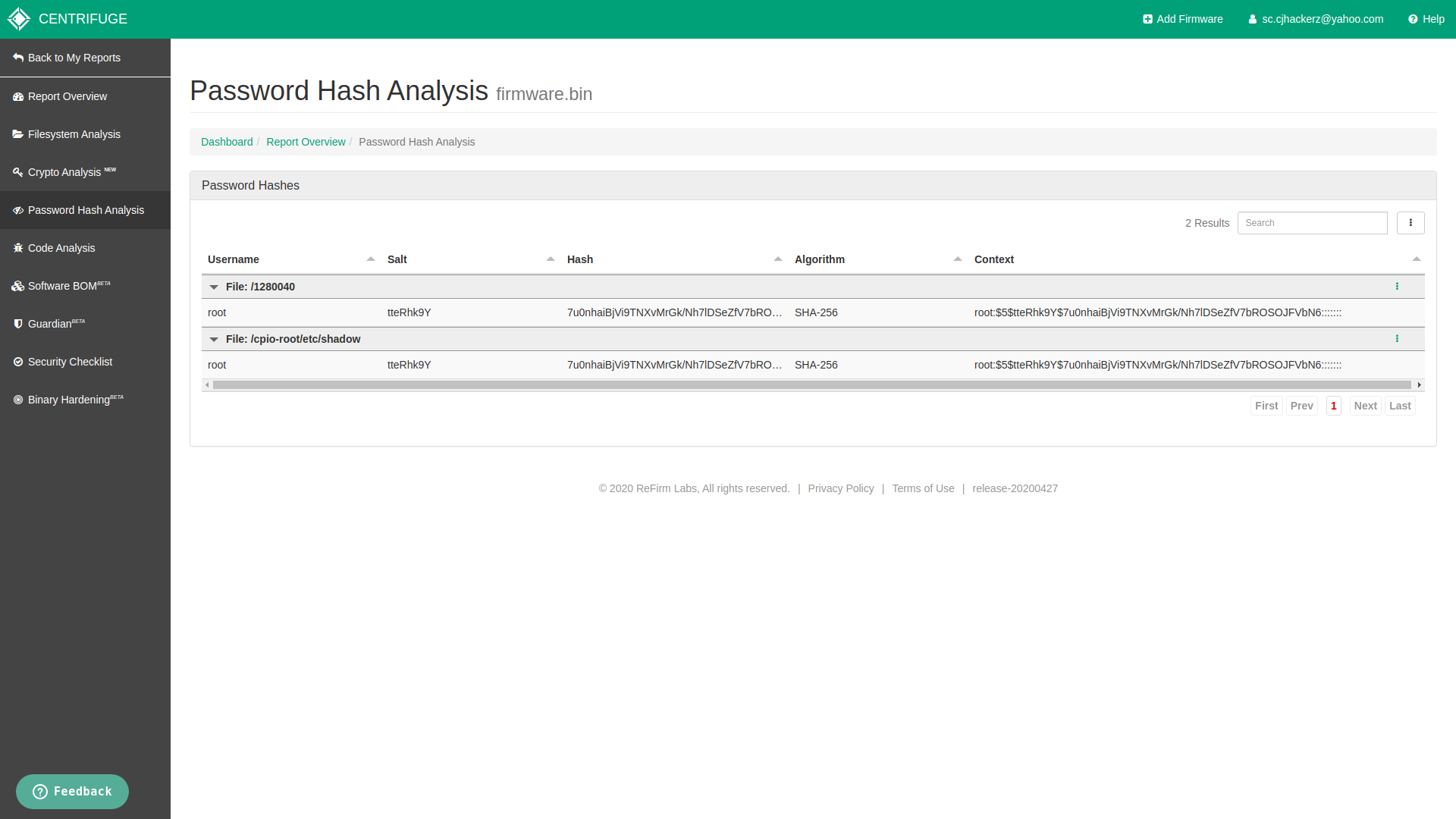
Root password hash from custom firmware
Code Analysis
The reason why I like centrifuge so much is because of this feature. This allows me to save a lot of time and tells me exactly where to look for vulnerabilities inside compiled .ELF binaries. Seriously because of it my big chuck of time can be saved for looking up vulnerable function calls manually using any cross platform dissasembler out there (Example: R2, Ghidra, IDA Pro etc.)
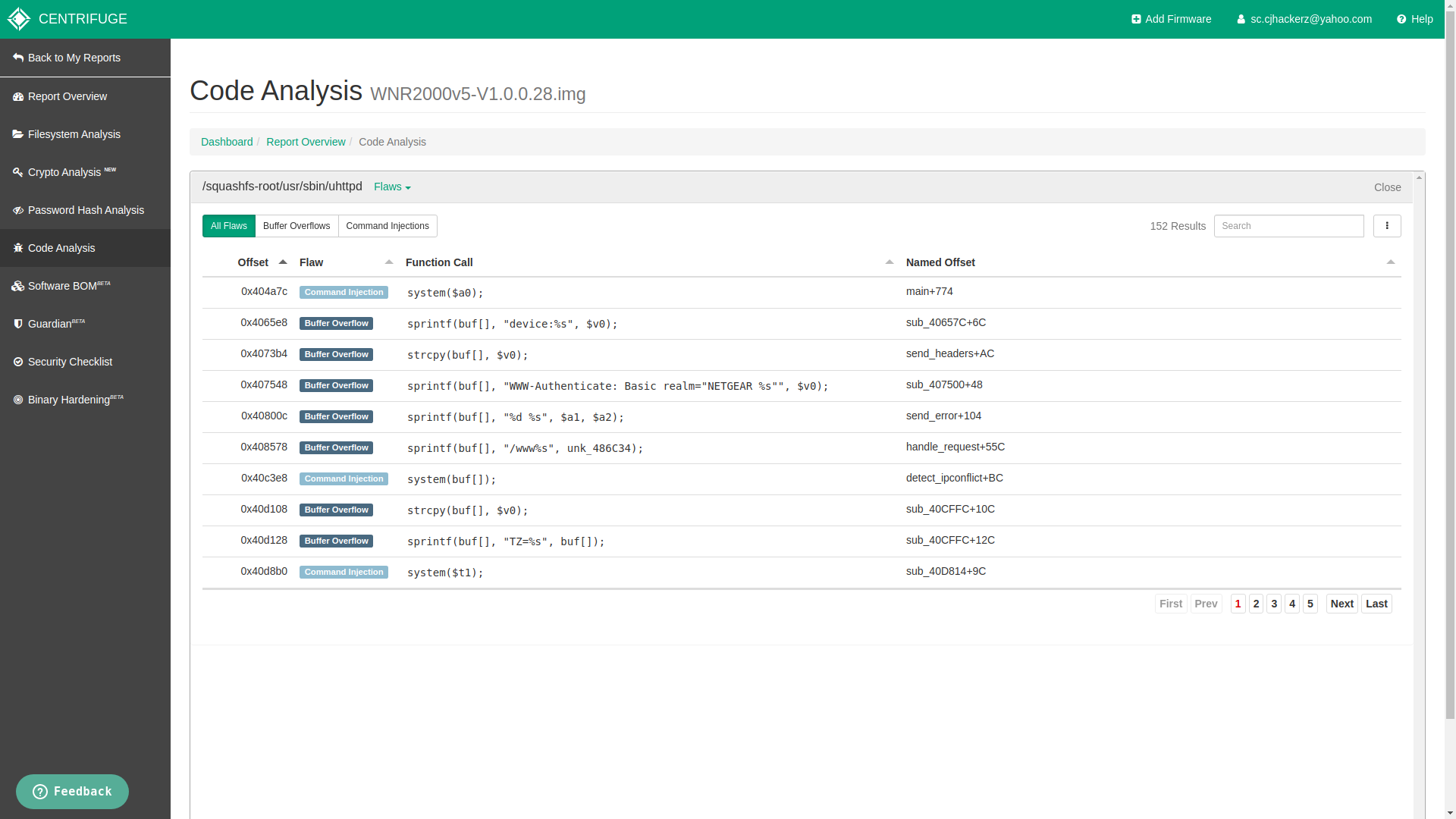
code analysis output
Software Bill of Materials
It lists out all software components included in firmware binary. This information is helpful during dynamic behaviour analysis of device. For example if you know there is tftp installed it means your device has file sharing feature that you can enable it and identify security flaws. This not a such complex feature anyone can do it manually by looking at binaries located at /bin /usr/bin /usr/sbin in extracted root filesystem.
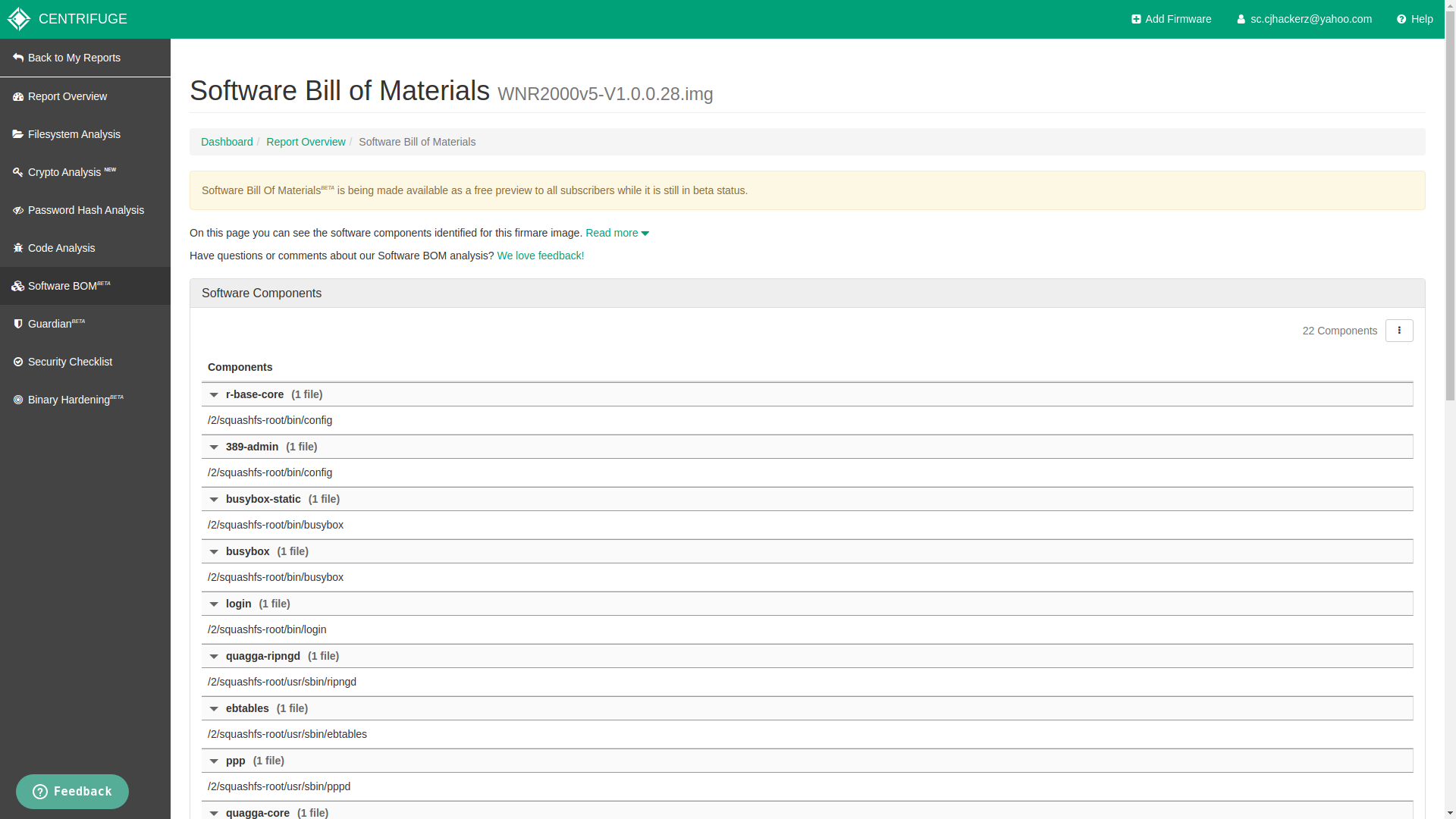
Software BOM
Centrifuge Guardian
This seem to find known vulnerabilities and listed CVE for software components inside firmware. Sadly it was not able to identify CVE-2016-10174 in Netgear firmware and it was my exact reason to pick up firmware version 1.0.0.28. It means Centrifuge Guardian don’t do CVE look up from model name of the device infact I tried to search all CVE for WNR2000v5 none was listed by it. I fully understand it’s beta software but this is very basic thing to do https://www.cvedetails.com/vulnerability-list/vendor_id-834/product_id-35931/Netgear-Wnr2000v5-Firmware.html.
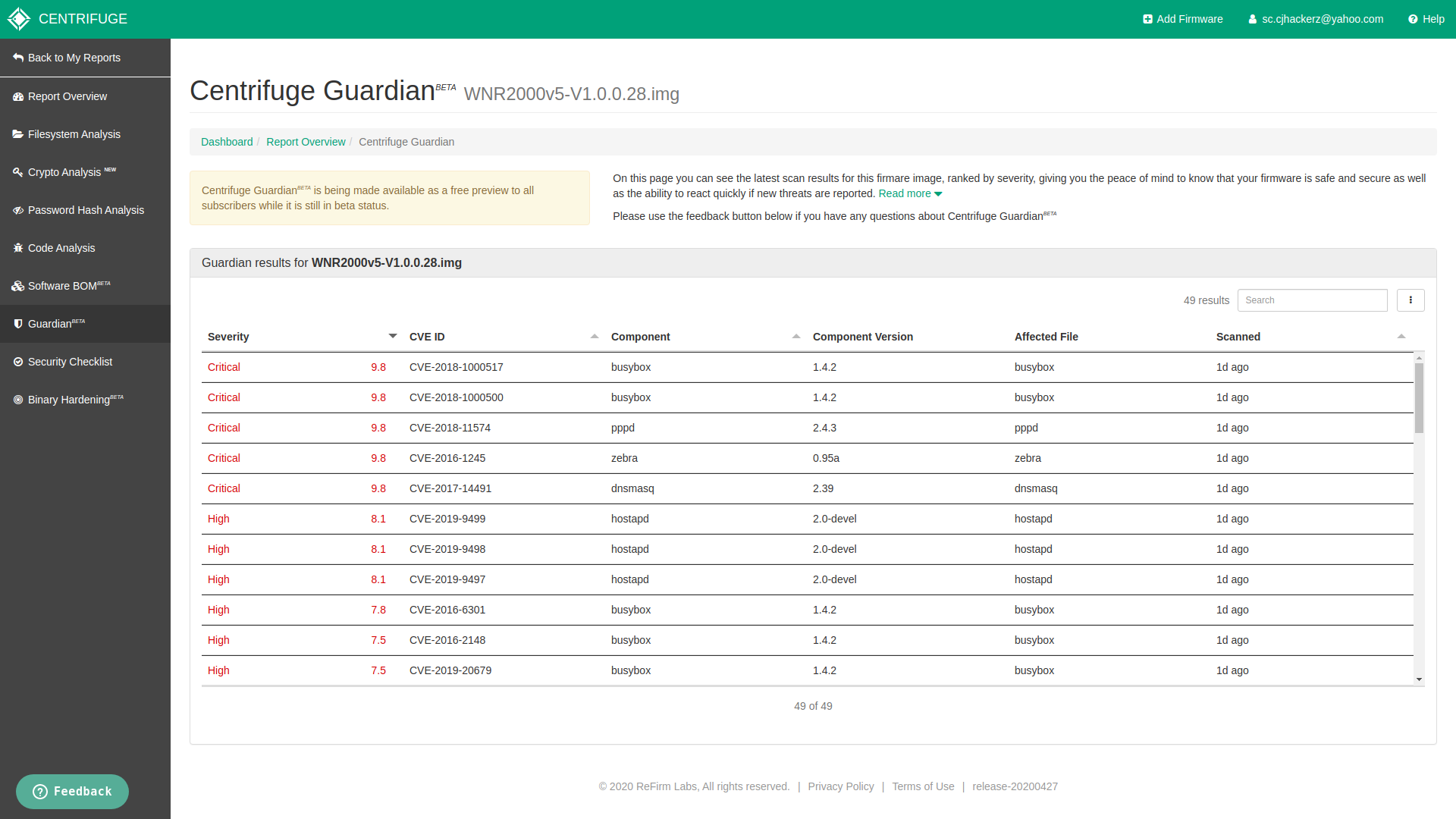
Centrifuge Guardian
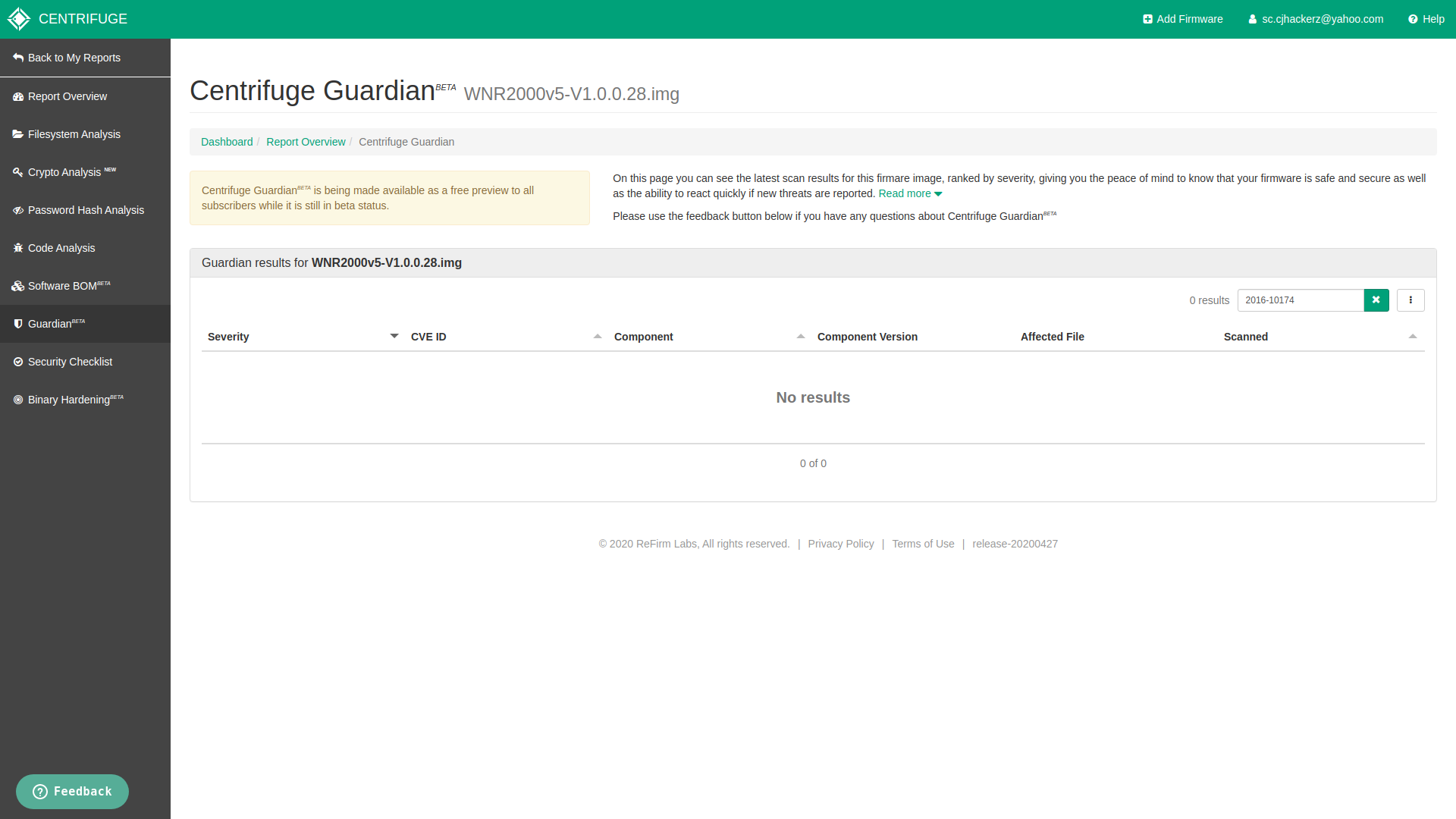
Custom CVE search
As expected for my custom firmware it did not detected any vulnerabilities since it has no software component at all. So I can confidently say Centrifuge Guardian is accurate CVE finder for given Software BOM.
Security Checklist
This feature is very basic and feels incomplete due to limited number security checks it does and there no way to customize them. Especially malware scanner, it only checks for only two Lojax and Mirai. There is no way to input your own yara rules or malware signatures for detection of other IoT botnet malwares like this one https://securitynews.sonicwall.com/xmlpost/linear-emerge-e3-access-controller-actively-being-exploited/. It’s good bonus feature although.
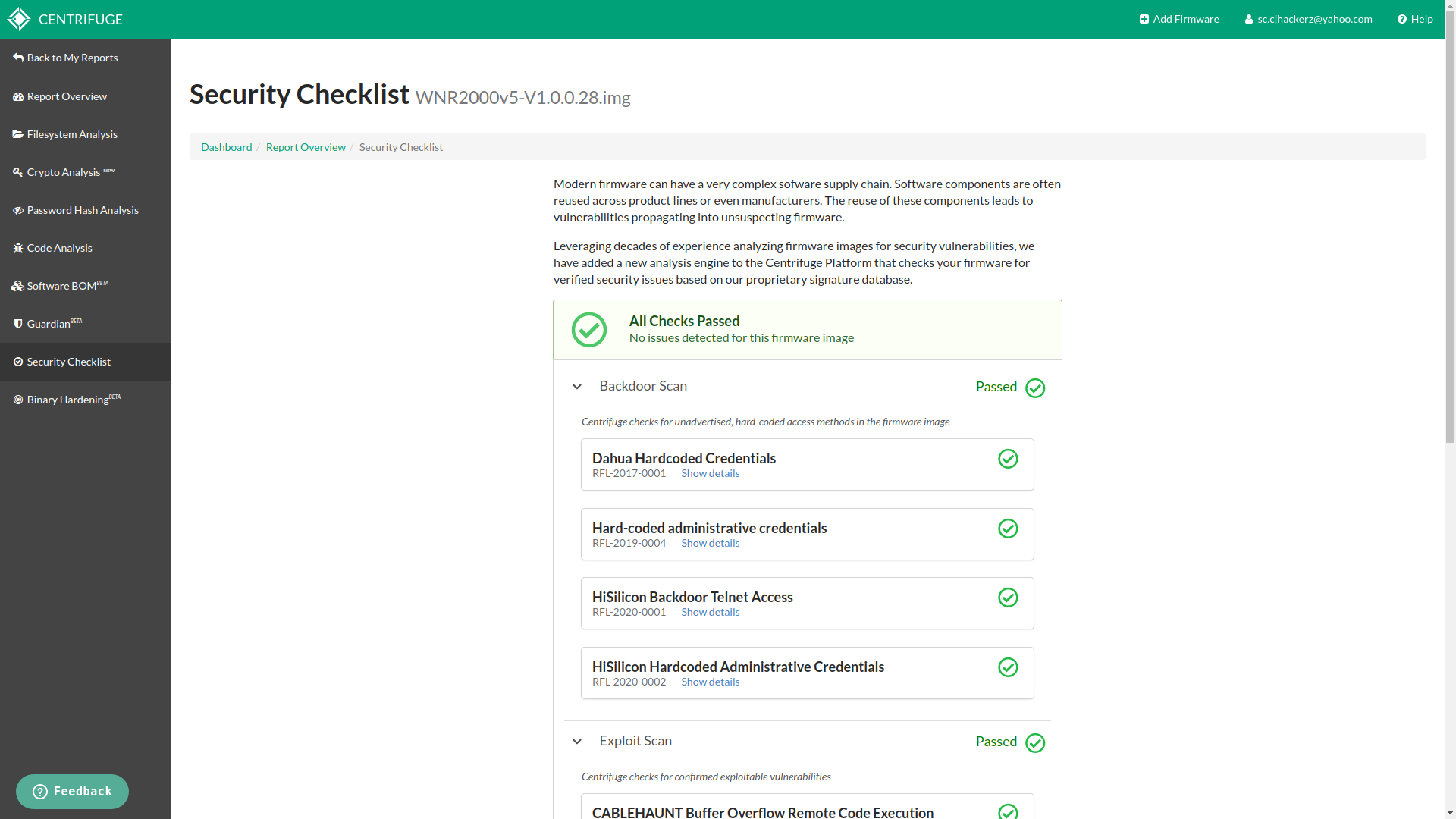
security checklist in action
Binary Hardening
There is good analysis on why IoT products uses less binary protections https://cyber-itl.org/2019/08/26/iot-data-writeup.html. One of the main reason is to increase performance and embeded hardware environments tends to have very limited amount of compute power. So many device vendors avoid enabling binary level protections. This can be prove danerous in case of on going adversary. More binary protections means more harder to develop exploit for that vulnerability. Having overview of binary hardening practices on given firmware gives idea about strength against active exploitation. Output from this feature is easy to understand.
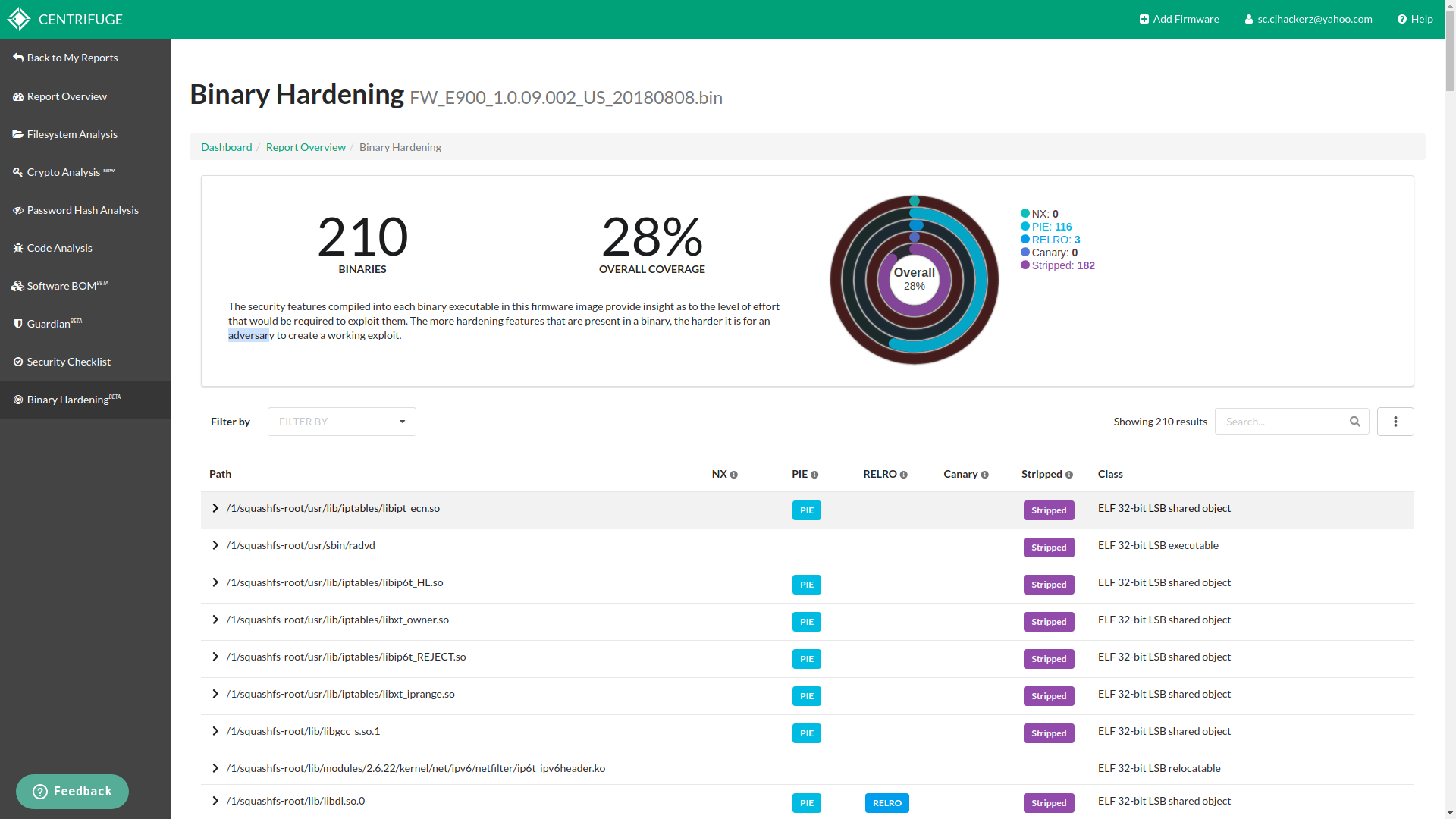
Hardening coverage on Linksys firmware
In my test run I had 4% hardening coverage for Netgear and for 28% coverage for Linksys which pretty much explains my intial point at start of this blog post.
Comparison with opensource alternative tool called FACT (the one which I use currently)
Now this section of review is for individual security research usecase. One my day to day job currently I use Firmware Analysis and Comparison Tool also known as FACT. It’s free and open source. Only problem with it is system requirements to run it is quite heavy. To run entire thing on single machine takes more than 8GB of RAM. And stable setup requires Ubuntu 18.04 which people rarely use in cybersecurity as well all stick to Kali Linux, Parrot OS and BlackArch. Due to opensource nature it provides lot’s of customization. The feature I like most from FACT which I want to see get implemented in Centrifuge as well is firmware comparision.
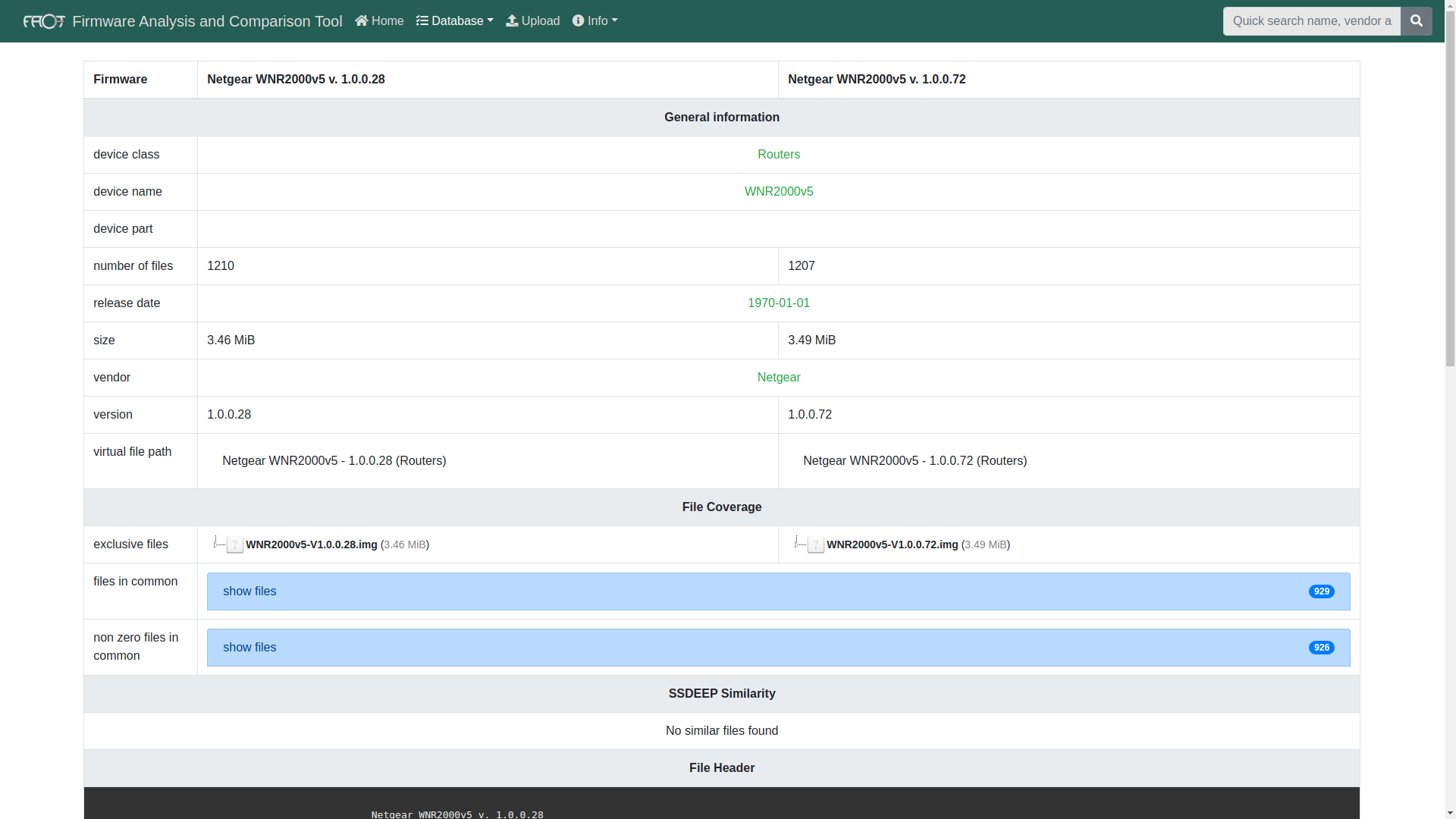
Comparison of two different firmware versions in FACT
Analysis in FACT can take upto 30min depending on number of options selected where as Centrifuge is pretty instant everything is done within 5min at max.
Centrifuge is closed source, for security of my data I completely have to trust ReFirm labs and I don’t know what kind code is being run on the infrastructure. What I feel is instead of keeping entire thing to yourself what you can do is make portions of Centrifuge open source let the folks in security community use it and improve the code base. That way you will have more trust and more creative minds working to improve product which has huge potnetial in IoT security. Just like it is being done with binwalk. This will also gain interest of bug bounty hunters as well.
Doing bug bounties in IoT security is hard we have to invest tons of money behind purchasing test hardware. So it becomes more hard for poor people like me with limited access to financial resources would avoid paying full licensing fees and turns themselves to open source alternative. If Centrifuge is provided as monthly subscription service (somthing like 10-20$/month) based acccess I would definatly ditch FACT for my daily usage.
In terms of stability FACT is pretty much unstable software where as due to huge financial backing of ReFirm labs Centrifuge is polished product.
Centrifuge found more number of CVEs in software components than FACT for the same firmware.
FACT has radare2 web-ui integration which allows me to eliminate false positives via manual analysis from external disassembler like R2, Centrifuge does not have anything like that implemented.
I am in love with reports generated by Centrifuge they are well presented with data. Reports generated in FACT is not well formatted. See the links at the end of this article to download them.
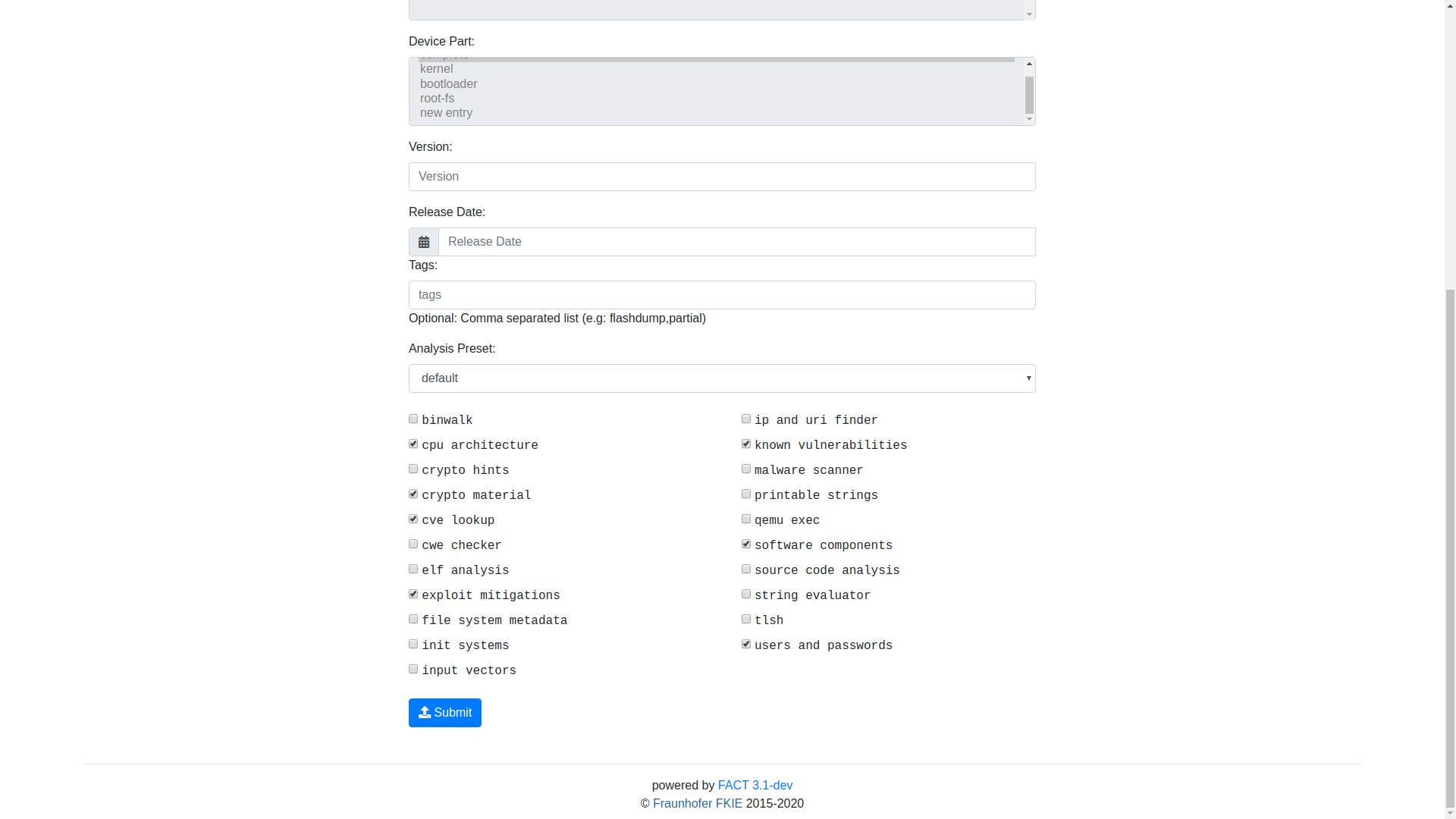
All other options in FACT
Verdict
Centrifuge means serious business, one with enough technical expertise I am definately sure you can uncover zero day flaws in given firmware. After reviewing everything price tag of feels justified for any organisation serious about IoT security. But ReFrim labs has to learn some more things from it’s opensource peers (FACT in my case) and bring those stuff to Centrifuge’s product ecosystem as well. Overall it’s quality platform. If I were CEO of the IoT security company with having enough revenue I would not have second thoughts of paying full price.
Pros:
- to the point good code analysis
- beautiful looking reports
- pretty instant
- well written API documentation
- don’t have to worry about infrastructure evrything is covered by ReFirrms Lab
Cons:
- missing support for custom malware/backdoor analysis with yara rules
- not free/open source
- no ip and url/endpoint finder
Lastly I want a feature get added to Centrifuge which will make it stand out in market. Which is nvram variables extratction from firmware. Nvram variables are crucial thing to know while setting up firmware emulation environments for dynamic analysis. Even FACT don’t have it as well. These variables can be often found in .ELF binaries or in init system start up scripts or in libnvram.so file. All you have to seek is nvram_get() function calls.
End
This is un-biased review, I was not paid by ReFrim labs to do it. FACT and Centrifuge both are good in their own position, I am not trying to spread negativity or create FUD about any of them. During entire article I was trying to provide constructive criticism based on known information. This my very first time writing review about something online at this great depth. If you like this article please share it online on social media platforms of your choice to make more people aware about firmware analysis platforms like Centrifuge and FACT.
